System Security Implementation
Diomidis Spinellis
Department of Management Science and Technology
Athens University of Economics and Business
Athens, Greece
dds@aueb.gr
System Security Roadmap
Welcome
System Security Implementation
Schedule
Παρασκευή 5 Νοεμβρίου 2004
- Έναρξη 15:00
- Διάλειμμα για φαγητό και καφέ: 16:30-17:00
- Μάθημα: 17:00-18:30
- Διάλειμμα για καφέ: 18:30-18:45
- Μάθημα: 18:45-19:30
Σάββατο 6 Νοεμβρίου 2004
- Έναρξη 09:00
- Διάλειμμα για καφέ: 10:30-10:45
- Μάθημα: 10:45-12:15
- Διάλειμμα για φαγητό και καφέ: 12:15-12:45
- Μάθημα: 12:45-13:30
Overview
- System Security Roadmap
- Welcome
- Overview
- Notes
- Security Infrastrucutre
- Security Infrastructure Investment
- Management Errors
- Security Mission Statement
- Security Awareness Training
- Security Support Personnel Duties
- Auditing
- Tools
- Targeted System Binaries And Directories
- Internet Attack Methods
- Incident Response
- Management-related Security Problems
- Software Installation Practices
- Authentication Practices
- Backup Practices
- Port Filtering Practices
- Auditing Practices
- Common Vulnerabilities
- Common Unix Vulnerabilities
- Common Windows Vulnerabilities
- Home-user Tips
- System Administrator Best Practices
- Low-cost Security Improvements
- Security Web Sites
- Security Books
- Cryptology
- Cryptology
- Algorithm Uses and Properties
- Algorithm Types
- Maintaining Confidentiality
- Transposition Ciphers
- Transposition Cryptanalysis
- Substitution Ciphers
- Polyalphabetic Ciphers
- Rotor Machines
- The Playfair Cipher
- SP Networks
- The Data Encryption Standard (DES)
- The Advanced Encryption Standard (AES)
- Operation Modes
- Electronic Code Book (ECB)
- Cipher Block Chaining (CBC)
- Output Feedback Mode (OFB)
- Hash Function Applications
- Asymmetric Ciphers
- The Diffie-Hellman Protocol
- Bibliography
- Access Control, Firewalls and VPNs
- Hardware-based Access Control
- Operating System Access Control
- Firewall Purpose
- Security Strategies
- Security by Obscurity
- Firewall Limitations
- Firewall Technologies
- Packet filtering
- Service Packet Filtering
- IP Packet Filtering
- Proxying
- Network Address Translation
- Firewall Architectures
- Incidents
- Maintenance
- VPN Architectures
- Tunneling
- Defence in Depth Example
- Bibliography
- Web Security, and Mobile Code
- Web Security Requirements
- User Privacy
- Malicious Applets
- The Java Sandbox Model
- ActiveX and Code Signing
- Javascript
- Cookies
- Protecting the Internet Explorer
- Protecting the Netscape Navigator
- User Authentication
- Application-layer Attacks
- Server Security and scripting
- State Variable Manipulation
- Cross-site Scripting
- Bibliography
- Software Security
- Principles for Software Security
- Buffer Overflows
- Unix Access Control
- Windows Access Control
- Race Conditions
- Randomness and Determinism
- Applying Cryptography
- Trust Management
- Password Authentication
- Database Security
- Application Security
- Bibliography
Notes
Security Infrastructure
- Management commitment
- Resources to back security policies and procedures
- Staff dedicated to security tasks
- Security mission statement
- Security awareness training program
- Security policies and procedures
- Clearly defined
- Implemented
- Documented
- Supplied to everyone within your organization
- Strong flow of information to and from the appropriate groups
- Security incident response team
- External and internal security perimeter controls
- Host and network based security auditing tools
Security Infrastructure Investment
Getting the management commitment
- Risk analysis
- Demonstrate threat (e.g. network sniffing)
probes.
- Run scanning tools against your network (be careful)
- Impact on company image
- Impact of DOS attack
- Information on other attacks
Management Errors
The 7 Top Management Errors that Lead to Computer Security Vulnerabilities
As determined by the 1,850 computer security experts and managers meeting at the SANS99 and Federal Computer Security Conferences held in Baltimore May 7-14, 1999
From
http://www.sans.org/newlook/resources/errors.htm (http://www.sans.org/newlook/resources/errors.htm)
- Pretend the problem will go away if they ignore it.
- Authorize reactive, short-term fixes so problems re-emerge rapidly
- Fail to realize how much money their information and organizational reputations are worth.
- Rely primarily on a firewall.
- Fail to deal with the operational aspects of security:
make a few fixes and then not allow the follow through necessary to ensure the problems stay fixed
- Fail to understand the relationship of information security to the business problem.
- Understand physical security but do not see the consequences of poor information security.
- Assign untrained people to maintain security and provide neither the training nor the time to make it possible to do the job.
Security Mission Statement
The security mission statement is determined by a number of factors:
- Security expectations of users and customers
- Customer loss by security breaches
- Customer loss by impaired functionality (due to security)
- Past down-time and monetary loss due to security incidents
- Insider threats
- User trust
- Local and remote access
- On-line sensitive or personal information
- Loss due to compromise or theft
- Different levels of security for different parts of your organization
- ERP systems
- Development
- Customer support
- Cost of negative publicity
- Existing security guidelines, regulations, or laws
- Conflict of business requirements and security
- Importance of confidentiality, integrity, availability
- Business needs
- Financial constraints
Security Awareness Training
- Use different media and formats
- Class
- Web
- Documentation
- Video
- Hands-on
- Part of new employee orientation
- Mock incidents (e.g. mail attachment)
- Circulate advisories and alerts
- Review procedures and content
Example of a CERT Advisory
Subject: CERT Summary CS-2002-02
Date: Tue, 28 May 2002 14:50:15 -0400 (EDT)
From: CERT Advisory <cert-advisory@cert.org>
Organization: CERT(R) Coordination Center - +1 412-268-7090
To: cert-advisory@cert.org
CERT Summary CS-2002-02
May 28, 2002
Each quarter, the CERT Coordination Center (CERT/CC) issues the CERT
summary to draw attention to the types of attacks reported to our
incident response team, as well as other noteworthy incident and
vulnerability information. The summary includes pointers to sources of
information for dealing with the problems.
Past CERT summaries are available at http://www.cert.org/summaries/.
______________________________________________________________________
Recent Activity
Since the last regularly scheduled CERT summary, issued in February
2002 (CS-2002-01), we have released several advisories addressing
vulnerabilties in Microsoft's IIS server, Oracle Database and
Application Servers, Sun Solaris cachefsd, and MSN Instant Messenger.
In addition, we have published statistics for the first quarter of
2002, numerous white papers, and a collection of frequently asked
questions about the OCTAVE Method.
For more current information on activity being reported to the
CERT/CC, please visit the CERT/CC Current Activity page. The Current
Activity page is a regularly updated summary of the most frequent,
high-impact types of security incidents and vulnerabilities being
reported to the CERT/CC. The information on the Current Activity page
is reviewed and updated as reporting trends change.
1. Exploitation of Vulnerabilities in Microsoft SQL Server
The CERT/CC has received reports of systems being compromised
through the automated exploitation of null or weak default sa
passwords in Microsoft SQL Server and Microsoft Data Engine. This
activity is accompanied by high volumes of scanning, and appears
to be related to recently discovered self-propagating malicious
code, referred to by various sources as Spida, SQLsnake, and
Digispid.
CERT Incident Note IN-2002-04:
Exploitation of Vulnerabilities in Microsoft SQL Server
http://www.cert.org/incident_notes/IN-2002-04.html
[...]
Security Support Personnel Duties
- Define, produce, and maintain official security policy and documentation
- Act as the organisation's personal data protection officer
- Recommend and develop internal security standards
- Monitor, audit, and test systems and networks for possible security problems
- Monitor (and respond to) security alerts, newsgroups, mailing lists, and postings.
- Review security log files on a daily basis and investigate anomalies as
needed
- Evaluate, procure, test, install, and maintain security infrastructure tools
- Test and install patches and fixes for security vulnerabilities in vendor
software
- Stay current on security technology and possible threats to your
organization
- Respond to security incidents
- Investigation
- Coordination
- Reporting
- Follow-up
- Liaise with law-enforcement officers
- Expert witness in legal proceedings
- Participate in reviews and analysis of internal projects
- Advocate corporate information security policy and procedures to
internal and external clients, customers, users, and staff
Security log example
Subject: istlab.dmst.aueb.gr security check output
Date: Sat, 15 Jun 2002 03:01:02 +0300 (EEST)
From: Charlie Root <root@istlab.dmst.aueb.gr>
To: undisclosed-recipients:;
Checking setuid files and devices:
Checking for uids
Checking setuid files and devices:
Checking for uids of 0:
root 0
toor 0
Checking for passwordless accounts:
istlab.dmst.aueb.gr kernel log messages:
> Jun 14 17:21:29 istlab su: dds to root on /dev/ttyp0
> Jun 14 23:30:02 istlab sendmail[65649]: g5EKU1a65648: Truncated MIME Content-Disposition header due to field size (length = 23) (possible attack)
istlab.dmst.aueb.gr login failures:
istlab.dmst.aueb.gr refused connections:
Coordination with ISP
Subject: Re: Prospatheia hacking
Date: Mon, 15 Jan 2001 12:49:33 +0200
From: OTEnet Network Abuse Team <abuse@otenet.gr>
To: Diomidis Spinellis <dds@host.gr>
On Mon, Jan 15, 2001 at 11:30:06AM +0200, Diomidis Spinellis wrote:
> Ο παρακάτω χρήστης σας προσπάθησε το Σάββατο να παραβιάσει το μηχάνημα
> XXX.XXX.XXX.XXX:
>
> Jan 13 01:28:17 inet popper[20009]: ddl@athe530-q166.otenet.gr: -ERR
> Unknown command: "close".
> Jan 13 01:28:19 inet popper[20009]: Possible probe of account ddl from
> host
> athe530-q166.otenet.gr
> Jan 13 01:28:31 inet popper[20010]: dds@athe530-q166.otenet.gr: -ERR
> Unknown command: "l".
> Jan 13 01:28:33 inet popper[20010]: dds@athe530-q166.otenet.gr: -ERR
> Unknown command: "r".
>
> Παρακαλώ να με ενημερώσετε για τις ενέργειές σας.
>
> Φιλικά,
>
> Δ. Σπινέλλης
--
Agaphte Kyrie
Meta apo e3etash twn log files pou mas exete steilei, exoume entopisei ton
syndromhth mas ekeino, o opoios empleketai sthn en logw apopeira kai exoume
pra3ei ta deonta prokeimenou na mhn epanalhfthoun sto mellon tetoies energeies
apo merous tou.
OTEnet Network Abuse Team
Complaint
Subject: [Spam mail]
Date: Tue, 22 Jan 2002 12:56:20 +0200
From: XXX@yyy.gr
To: abuse@isp.gr
CC: abuse@host.gr
Aytos fainetai (me traceroute) oti pairnei grammh apo esas. Epeidh oi idioi
einai spammers sas stelnw esas to complaint.
To spam einai attached.
Eyxaristw.
--
[Copy of the spam mail]
Auditing
Help an organization balance resources expended against the most likely areas of weaknesses.
| Audit Type | Reason |
| New System Installation Security Audits |
Ensure conformance to existing policies and a standard system configuration. |
| Regular Automated System Audit Checks |
Reveal a "visitation" by an intruder or illicit activity by insiders. |
| Random Security Audit Checks |
- Test for conformance to security policies and standards (by finding illicit activity) ,
- Check for the existence of a specific class of problems (e.g., the presence of a vulnerability reported by a vendor).
|
| Nightly Audits of Critical Files |
- Assess the integrity of critical files (e.g., the password file)
- Integrity of databases (e.g., payroll or sales and marketing information).
|
| User Account Activity Audits |
Detect dormant, invalid, misused accounts. |
| Periodic audits and vulnerability assessments |
Determine overall state of your security infrastructure. |
Tools
- Host-based Auditing Tools:
COPS, NCARP, crack, Tiger, Tripwire, logcheck, tklogger, Safesuite, NetSonar
- Network Traffic Analysis & Intrusion Detection Tools:
tcpdump, synsniff, NetRanger, NOCOL, NFR, RealSecure, Shadow
- Security Management and Improvement Tools:
crack, localmail, smrsh, logdaemon, npasswd, op, passwd+, S4-kit, sfingerd, sudo, swatch, watcher, wuftpd, LPRng
- Firewall, Proxy amd Filtering Tools:
fwtk, ipfilter, ipfirewall, portmap v3, SOCKS, tcp_wrappers, smapd
- Network-Based Auditing Tools:
nmap, nessus, SATAN, Safesuite
- Encryption Tools:
md5, md5check, PGP, rpem, UFC-crypt
- One-Time Password Tools:
OPIE, S/Key
- Secure Remote Access and Authorization Tools:
RADIUS, TACACS+, SSL, SSH, Kerberos
Targeted System Binaries And Directories
- System binaries:
- /bin/login
- /usr/etc/in.telnetd
- /usr/etc/in.ftpd
- /usr/etc/in.tftpd
- /usr/ucb/netstat
- /bin/ps
- /bin/ls
- /usr/sbin/ifconfig
- /bin/df
- /usr/lib/libc.a
- /usr/lib/*.so
- /usr/ucb/cc
- Files:
- /.rhosts
- /etc/hosts.equiv
- /bin/.rhosts
- /etc/passwd
- /etc/group
- /var/yp/* (nis maps)
- root environment files (.login, .cshrc, .profile, .forward)
- Hidden files:
- Starting with .
- /tmp
- /var/tmp
- /etc/tmp
- /usr/spool
- /usr/lib/cron
- Modified files:
- /var/log/messages
- /var/log/wtmp
- /var/log/lastlog
- /var/account/*
Internet Attack Methods
- Exploitation of vulnerabilities in vendor programs.
- Exploitation of cgi-bin vulnerabilities.
- Email bombing, spamming and relaying through other sites.
- Exploitation of misconfigured anonymous FTP and web servers.
- Exploitation of named/BIND vulnerabilities.
- Exploitation of mail transfer agents and mail readers.
- Denial of Services (DoS) attacks using various methods.
- Sending hostile code and attack programs as mail attachments or browsed
page contents.
Incident Response
- Don't panic!
- Evaluate the situation
- Has attacker succeeded?
- Is the attack in progress?
- Follow your organizations policies and procedures,
- Use the appropriate chain of command when notifying other people or organizations.
- Contact incident response agencies appropriate for your site
- Make communication via an out-of-band method (e.g., a phone call) to ensure intruders do not intercept information.
-
Document your actions
- persons contacted
- phone calls made
- files modified
- system jobs stopped
- Snapshot the system
-
Make copies of files the intruders may have left or touched and store them off-line.
-
If you are unsure of what actions to take, seek additional help and guidance before removing files or halting system processes.
- Involve security department
- Physical access
- Insider
- Law enforcement officers
- Plan
Incident Response Centers
CERT(sm) Coordination Center
http://www.cert.org/
email cert@cert.org or call +1 412 268-7090
GRNET-CERT
Computer Emergency Responce Team
for the Greek National Research Network
E-Mail: grnet-cert@grnet.gr (mailto:grnet-cert@grnet.gr)
Network Operations Center, University of the Aegean, 30 Voulgaroktonou str, Athens 114 72, Greece
Telephone: +30 - 210 - 649 - 2056
Telefax: +30 - 210 - 649 - 2499
World Wide Web:
http://cert.grnet.gr (http://cert.grnet.gr)
Network Management Center
National Technical University of Athens
Iroon Polytechnioy 9
Zografou, GR 157 80
Athens
Greece
phone [+30-210] 772.1860
fax [+30-210] 772.1866
http://www.ntua.gr/grnet-cert/grnet-cert.html (http://www.ntua.gr/grnet-cert/grnet-cert.html)
Management-related Security Problems
- No dedicated staff
- Insufficient resources
- Lack of management support
- Staff with no authority to deploy appropriate security measures
- Failure to install vendor patches for known security problems.
- No monitoring and restricting network access to internal hosts.
- Not using sufficient authentication and authorization systems for remote access.
- Failure to implement or enforce procedures and standards when installing new devices on the network.
- Security through obscurity
Software Installation Practices
Modify default software installation to
- remove unnecessary software,
- turn off unneeded services,
- close extraneous ports.
Develop standard installation guidelines for all operating systems and applications used by the organization.
Authentication Practices
- Audit the accounts on your systems and create a master list
- Develop procedures for adding authorized accounts to the list, and for removing accounts when they are no longer in use.
- Validate the list on a regular basis to make sure no new accounts have been added and that unused accounts have been removed.
- Run a password cracking tool against the accounts looking for weak or no passwords. (Make sure you
have official written permission before employing a password cracking tool.)
- Train users
- Install password checking tools
- Use alternative authentication methods
Backup Practices
- Inventory critical systems
- Are there backup procedures for those systems?
- Is the backup interval acceptable?
- Are those systems being backed up according to the procedures?
- Has the backup media been verified to make sure the data is being backed up accurately?
- Is the backup media properly protected in-house and with off-site storage?
- Are there copies of the operating system and any restoration utilities stored off-site (including necessary
license keys)?
- Have restoration procedures been validated and tested?
Port Filtering Practices
- Configure router
- Install a firewall
- Use a port scanner (e.g. nmap, netstat)
- Turn-off services (/etc/inetd.conf, /etc/rc*, services)
Evaluating Vulnerabilities
For each vulnerability we need to now:
- Systems impacted
- How to determine if we are vulnerable
- How to protect against it
Common Unix Vulnerabilities
- U1 BIND Domain Name System
- U2 Web Server
- U3 Authentication
- U4 Version Control Systems
- U5 Mail Transport Service
- U6 Simple Network Management Protocol (SNMP)
- U7 Open Secure Sockets Layer (SSL)
- U8 Misconfiguration of Enterprise Services NIS/NFS
- U9 Databases
- U10 Kernel
(From the Twenty Most Critical Internet Security Vulnerabilities
2004
Copyright 2001-2004, The SANS Institute
http://www.sans.org/top20.htm (http://www.sans.org/top20.htm))
Common Windows Vulnerabilities
- W1 Web Servers and Services
- W2 Workstation Service
- W3 Windows Remote Access Services
- W4 Microsoft SQL Server (MSSQL)
- W5 Windows Authentication
- W6 Web Browsers
- W7 File-Sharing Applications
- W8 LSAS Exposures
- W9 Mail Client
- W10 Instant Messaging
(From the Twenty Most Critical Internet Security Vulnerabilities
2004
Copyright 2001-2004, The SANS Institute
http://www.sans.org/top20.htm (http://www.sans.org/top20.htm))
Home-user Tips
(Excerpted from http://www.nipc.gov/warnings/computertips.htm (http://www.nipc.gov/warnings/computertips.htm))
- Use strong passwords.
- Make regular backups of critical data.
- Use virus protection software.
- Use a firewall as a gatekeeper between your computer and the Internet.
- Do not keep computers online when not in use.
- Do not open e-mail attachments from strangers or suspicious attachments.
- Regularly download security patches from your software vendors.
System Administrator Best Practices
- Knowledge update
- System and console - physical security
- Keep your systems lean and mean
- Superuser password
- Delegating superuser tasks
- User passwords
- User terminals
- Restrict users (shell, remote access)
- User education
- Keep your systems up to date
- Vulnerability testing
- Monitor your systems periodically
- Configuration documentation
- Backup and disaster recovery
Low-cost Security Improvements
Doing it on a shoestring basis:
- Document and publish what you expect your system support staff to do with respect to security.
- Configure your border routers to deny all unnecessary incoming traffic.
- Identify and protect your most valuable assets first.
- Secure the perimeter and core systems.
- Simplify.
- Use freeware vulnerability assessment tools to conduct a self-assessment of your network and
computers. Publish the results internally to management staff.
- Install freeware host and network based auditing and traffic analysis tools on critical hosts.
- Monitor output and logs on a daily basis.
Free Tool Repositories
Security Web Sites
Security Books
-
Firewalls and Internet Security by Bill Cheswick and Steve Bellovin
-
Practical UNIX and Internet Security, 2nd Edition by Simson Garfinkel and Gene Spafford
- Ross Anderson.
Security Engineering: A Guide to Building Dependable Distributed Systems.
John Wiley & Sons, New York, 2001.
- Friedrich L. Bauer.
Decrypted Secrets: Methods and Maxims of Cryptology.
Springer Verlag, 1997.
- Dorothy Elizabeth Robling
Denning.
Cryptography and Data Security.
Addison-Wesley, 1983.
- Peter J. Denning.
Computers Under Attack: Intruders, Worms, and Viruses.
Addison-Wesley, 1990.
- Tom Forester and
Perry Morrison.
Computer Ethics: Cautionary Tales and Ethical Dilemmas in Computing.
MIT Press, Cambridge, 1990.
- Dieter Gollmann.
Computer Security.
John Wiley & Sons, New York, 1999.
- Michael Howard and
David LeBlanc.
Writing Secure Code.
Microsoft Press, Redmond, WA, second edition, 2003.
- David Kahn.
The
Codebreakers: The Story of Secret Writing.
Scribner, New York, 1996.
- Gary McGraw and
Edward W. Felten.
Securing Java: Getting Down to Business with Mobile Code.
Wiley, New York, 1999.
- Peter G. Neumann.
Computer Related Risks.
Addison-Wesley, 1995.
- David L.
Oppenheimer, David A. Wagner, and Michele D. Crabb.
System Security: A Management Perspective.
Short Topics in System Administration. USENIX Association, Berkeley, CA,
1997.
- Eric Rescorla.
SSL
and TLS.
Addison-Wesley, 2001.
- Aviel D. Rubin, Daniel
Geer, and Marcus J. Ranum.
Web
Security Sourcebook.
John Wiley & Sons, New York, 1997.
- Bruce Schneier.
Applied Cryptography.
Wiley, New York, second edition, 1996.
- Bruce Schneier.
Secrets & Lies: Digital Security in a Networked World.
Wiley Computer Publishing, New York, 2000.
- John Viega and Gary
McGraw.
Building Secure Software: How to Avoid Security Problems the Right Way.
Addison-Wesley, 2001.
- Elizabeth Zwicky, Simon
Cooper, and D. Brent Chapman.
Building Internet Firewalls.
O'Reilly and Associates, Sebastopol, CA, second edition, 2000.
Articles
- Anish Bhinami.
Securing the commercial internet.
Communications of the ACM, 39(6):29–35, June 1996.
- Huseyin Cavusoglu,
Birendra Mishra, and Srinivasan Raghunathan.
Model for evaluating security investments.
Communications of the ACM, 47(7):87–92, July 2004.
- Commission of the European Communities.
Glossary of information systems security.
DGXIII, INFOSEC Programme/S2001, 1993.
- Commission of the European Communities.
Risk analysis methods database.
DGXIII, INFOSEC Programme/S2014, 1993.
- United Kingdom Central Computer
and Telecommunication Agency, United Kingdom.
CCTA Risk Analysis and Management Method: User Manual., version
3.0 edition, 1996.
HMSO.
- Eric Dubois and Suchun Wu.
A framework for dealing with and specifying security requirements in
information systems.
In Sokratis K. Katsikas and Dimitris Gritzalis, editors, Information
Systems Security: Facing the information society of the 21st century,
pages 88–99. Chapman & Hall, 1996.
- C. Ellison and
B. Schneier.
Ten risks of pki: What
you're not being told about public key infrastructure.
Computer Security Journal, 16(1):1–7, 2000.
- J. H. P. Eloff,
L. Labuschagne, and K. P. Badenhorst.
A comparative framework for risk analysis methods.
Computers & Security, 12(6):597–603, October 1993.
- M. E. Kabay.
The NCSA Guide ot Enterprise Security: Protecting Information
Assets.
McGraw-Hill, 1996.
- Ravi Sandhu, Edward
Coyne, Hal Feinstein, and Charles Youman.
Role-based access control: A multi-dimensional view.
In 10th Annual Computer Security Applications Conference, pages
54–62. IEEE Computer Society Press, 1994.
- Richard G. Wilsher and
Helmut Kurth.
Security assurance in information systems.
In Sokratis K. Katsikas and Dimitris Gritzalis, editors, Information
Systems Security: Facing the information society of the 21st century,
pages 74–87. Chapman & Hall, 1996.
Cryptology
Cryptology
- Cryptography:
-
Generalized methods to hide (encrypt) and authenticate information
- Cryptanalysis:
-
Generalized methods to expose and substitute information
Algorithm Uses and Properties
-
Algorithms reversibly converting data (plaintext) into unintelligible form (ciphertext).
- E(P) = C, and then D(C) = P
- Only knowledge of "secret" allows recovery.
- Kerckhoffs's doctrine (19th century):
not based on the secrecy of the algorithm.
- E(P, EK) = C, and then D(C, DK) = P
- Building blocks for services/protocols that provide other assurances such as
- confidentiality
- integrity
- authentication
- non-repudiation
Algorithm Types
Algorithm applications
- Confidentiality
- Block Ciphers: we encrypt several plaintext symbols at once in a block
- Stream Ciphers: the encryption rule depends on a plaintext symbol's position in the stream of plaintext symbols.
- Authenticity and non repudiation:
- Hash Functions
- Digital Signatures
Maintaining Confidentiality
- One time pad (OTP)
- length of key equal to message length
- c = m XOR k
- c XOR k = m
- perfect secrecy
- severe key distribution problems
- Shared secret key
- c = E(m,k).
- D(c,k) = m
- requires key distribution
- vulnerable to exhaustive key search
- Private / public key
- Key generator creates Ek, Dk
- c = E(m, Ek)
- D(c, Dk) = m
- Computationally expensive
Transposition Ciphers
- Re-arrange order of letters
- Write-in in a geometrical figure (square, scytale)
- Take-off in a specified order
- Key is the figure and the order
Example
1 2 3 4
T R A N
S P O T
I T I O
N X X X
Take-off as 2, 4, 3, 1: RPTXNTOXAOIXTSIN
Try RAYXPAIXYNSXCTLS
Transposition Cryptanalysis
- Recognize by noting relative frequencies
(same as in natural language)
- English: ... f m u c d h l r s n a I o t e
- Greek ... π λ μ ν σ ε κ σ ρ
τ ι ο α
- Use digraph and trigraph frequency distributions
Substitution Ciphers
- Shifted alphabets
- C = P + K mod 26
- Caesar Cipher (K=3)
- Key is the shift
- Cipher alphabet
- Key is the substitution alphabet
- Cryptanalysis: Single letter frequency analysis
Polyalphabetic Ciphers
Rotor Machines
- Each rotor maps 26 characters on the front face to 26 on the back face
- Simple substitution cipher
- After each encoding rotation changes the mapping
- Introduces polyalphabetic element with period 26
- The output of one rotor feeds the next
- Introduces function composition
- The key is the rotor wiring, placement, and initial position
- Used by the Germans during the WW2
- Cryptanalyzed by the British using electromechanical computers

The Playfair Cipher
Example:
A -> B
B -> I
O -> P
R -> U
T -> A
X -> V
L -> O
A -> I
N -> L
D -> G
I -> Y
N -> L
G -> H
X -> W
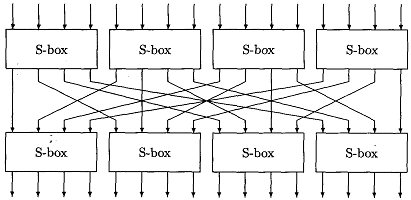
SP Networks
- To increase block size we need (prohibitively) larger tables
- As an example a function 16 -> 16 bits would
require a table of 220 bits (16 * 216).
- A substitution permutation network requires a lot less
storage
- Data has to pass through the network multiple times to add
diffusion and confusion to the plaintext
- Result is called a product cipher
Example: 4 bit S-box design with a single permutation
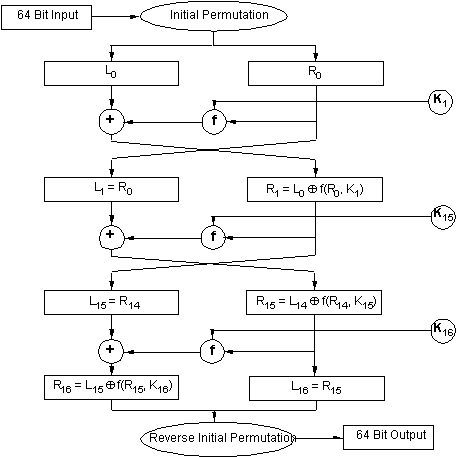
The Data Encryption Standard (DES)
- 64 bit input and output
- 56 bit key (marginal length; vulnerable to exhaustive key search)
- Standard for encryption of unclassified data since 1977
- 16 internal rounds
DES structure
The Advanced Encryption Standard (AES)
- Result of a public process
- Evaluation criteria:
- Security
- No licensing
- Computational efficiency
- Memory requirements
- Flexibility (key size, block size, time/memory tradeoffs)
- Hardware and software suitability
- Simplicity of design
- Acts on 128-bit blocks
- Key 128, 192 or 256 bits (for 10, 12, 14 rounds)
Operation Modes
Block ciphers can be operated in a number of different modes
- Electronic code book (ECB)
- Cipher block chaining (CBC)
- Output feedback mode (OFB)
Electronic Code Book (ECB)
- Each block is separately encoded
- Same blocks result in same ciphertext
- Can be used to locate known plaintext (e.g. blanks)
- Subject to cut and splice attacks
Cipher Block Chaining (CBC)
- Each plaintext block is XORed with the previous encrypted block
Cn = E(Pn XOR Cn - 1, K)
- Patterns in plaintext are concealed
- An error is only propagated one block
- Can do random access decryption
(one block look backwards required)
- Subject to some cut and splice attacks
- Last block can be used as a
message authentication code (MAC)
since it depends on all the message and the key
Output Feedback Mode (OFB)
- An initial vector is encoded N times
- The result of each encoding is used to XOR a message block
- Allow pre-computing of pseudorandom stream
- No error propagation problem as in CBC
- Allow in-time encrypt/decrypt due to bit-wise computation
- Subject to known-plaintext substitution attacks:
Knowing Pi allows you to recover Ki and
substitute Ci with Ci'
Hash Function Properties
Hash functions compress a n (abritrarily) large number of bits
into a small number of bits (e.g. 512).
Properties
- One way; can not be reversed
- Output does not reveal information on input
- Hard to find collisions (different messages with same hash)
Common Hash Functions
- Block cipher in CBC mode
- SHA1 (secure hash algorithm) 160-bit output
- MD5 (message digest) 128-bit output
- SHA256 SHA512 (secure hash algorithm) 256/512-bit output
Hash Function Applications
- Construct a message authentication code (MAC)
- Digital signature
- Make commitments, but reveal message later
- Timestamping
- Key updating: key is hashed at specific intervals resulting in new key
Asymmetric Ciphers
- Key is split into private and public part
- Public key can not be used to derive private key
- Encryption is performed using the public key
- Decryption is performed using the private key
- The two operations can be combined to establish secrecy and sender authenticity
- Can be used to implement a digital signature
- Underlying mathematical operations
- Factorization (factor a product of two primes)
- Discrete logarithm (calculate the integer nth root of a number)
- Elliptic curves
- Computationally expensive
- Typically used to establish common secret key
The Diffie-Hellman Protocol
- Can be used to establish common secret key over insecure channel
- Requires commutative encryption function E(E(M, Ka), Kb) = E(E(M, Kb), Ka)
- Procedure
- Alice chooses a key M
- Alice sends Bob E(M, Ka)
- Bob sends Alice E(E(M, Ka), Kb)
- ... which is E(E(M, Kb), Ka)
- Alice decrypts it into E(M, Kb) and sends it to Bob
- Bob decrypts it to M
- M can then be used as a shared secret key
Case Study: Public Key Cryptography
The following example is based on the
OpenSSL (http://www.openssl.org/) open-source cryptography
library and command-line tool.
#!/bin/sh
################
# Key generation
# Create Alice's key pair
openssl genrsa >alice.private
# Obtain Alice's public key
openssl rsa -pubout <alice.private >alice.public
# Create Bob's key pair
openssl genrsa >bob.private
# Obtain Bob's public key
openssl rsa -pubout <bob.private >bob.public
##########################################
# Alice sends a short confidential message
# Secret message Alice wants to send to Bob
echo "Alice loves you" >message.plain
# Alice encrypts the message using Bob's public key
openssl rsautl -encrypt -in message.plain -out message.encrypted -pubin -inkey bob.public
# Bob decrypts Alice's message using his private key
openssl rsautl -decrypt -in message.encrypted -out message.decrypted -inkey bob.private
##################################
# Bob sends a short signed message
# Message Bob wants to sign
echo "Will you marry me?" >message.plain
# Bob signs the message using his private key
openssl rsautl -sign -in message.plain -out message.signed -inkey bob.private
# Alice verifies Bob's message using his public key
openssl rsautl -verify -in message.signed -out message.verified -pubin -inkey bob.public
#####################################################
# Alice sends a large signed and confidential message
# Secret message Alice wants to send to Bob
cat >message.plain <<EOF
Marital AGREEMENT
THIS AGREEMENT, made this thirteen day of June, 2004 is between Bob
and Alice
1. PURPOSE. The parties expect to be married to death do them part,
and hear by enter into this agrement vouluntarily.
2. EFFECT OF AGREEMENT. The parties agree that if one or the other
commits infidelity during the duration of the marriage, that the person
guilty of said act shall in effect and wholey forsake all material
property, assets and rights to act as a parent of any children.
3. DEFINITON OF INFEDELITY. Infedelity is defined as follows: Any
socializing with the intent to establish a realtionship, and/or
physical contact with other person.
4. JOINT PROPERTY, ETC. This Agreement does not restrict, prohibit
or condition any conveyance or transfer by the parties, or either of
them alone, of the Separate Property of either party into tenancy in
common, joint tenancy, tenency by the entireties or any other form of
concurrent and/or undivided estate or ownership between the parties,
or the acquisition of any property in any such form of ownership by the
parties. The incidents and attributes of ownership and other rights
of the parties with respect to any property so conveyed, transferred
or acquired shall be determined under State law and shall not be
governed by or otherwise determined with reference to this Agreement.
5. SEPARATE PROPERTY. The parties agree that there is no seperate
property.
6. WAIVER OF RIGHTS. Except as otherwise provided in this Agreement,
each party hereby waives, releases and relinquishes any and all right,
title or interest whatsoever, whether arising by common law or present
or future statute of any jurisdiction or otherwise.
7. DISSOLUTION/SEPARATION/ANNULMENT. Except as otherwise provided in
this Agreement, each party specifically agrees that neither shall make
any claim for or be entitled to receive any money or property from
the other as alimony, spousal support, or maintenance in the event
of separation, annulment, dissolution or any other domestic relations
proceeding of any kind or nature, and each of the parties waives and
relinquishes any claim for alimony, spousal support or maintenance,
including, but not limited to, any claims for services rendered,
work performed, and labor expended by either of the parties during
any period of cohabitation prior to the marriage and during the entire
length of the marriage. The waiver of spousal support shall apply to
claims both pre and post-judgment.
8. RIGHT TO CONTEST. Nothing contained herein shall limit the right
of either party to contest any domestic relations suit between the
parties or to file a countersuit against the other party; However,
in any hearing on such suit, this Agreement shall be considered
a full and complete settlement of all property rights between the
parties. In such case, neither party shall maintain any claim or demand
whatsoever against the other for property, suit money, attorney fees
and costs which is either inconsistent with or not provided for in
this Agreement.
9. INTEGRATION. This Agreement sets forth the entire agreement between
the parties with regard to the subject matter hereof. All prior
agreements, covenants, representations, and warranties, expressed or
implied, oral or written, with respect to the subject matter hereof,
are contained herein. All prior or contemporaneous conversations,
negotiations, possible and alleged agreements, representations,
covenants, and warranties, with respect to the subject matter hereof,
are waived, merged, and superseded hereby. This is an integrated
agreement.
10. BINDING ON SUCCESSORS. Each and every provision hereof shall
inure to the benefit of and shall be binding upon the heirs, assigns,
personal representatives, and all successors in the interest of
the parties.
11. ACKNOWLEDGEMENTS. Each party acknowledges that he or she has
had an adequate opportunity to read and study this Agreement, to
consider it, to consult with attorneys individually selected by each
party, without any form of coercion, duress or pressure. Each party
acknowledges that he or she has examined the Agreement before signing
it, and has been advised by independent legal counsel concerning the
rights, liabilities and implications of this document.
12. STATE LAW. It is intended that this Agreement be valid and
enforceable within the provisions of the State Law, and that Case
Law that governs its interpretation. State law is considered to be
that of California, USA.
EOF
# Alice generates a short random key to be used for encrypting the message
openssl rand 16 -out key.plain
# Alice encrypts the message with the short random key
openssl des3 -e -kfile key.plain -in message.plain -out message.encrypted
# Alice creates a message digest of the message to sign
openssl dgst -binary message.plain >message.digest
# Alice signs the digest using her private key
openssl rsautl -sign -in message.digest -out digest.signed -inkey alice.private
# Alice encrypts the random key using Bob's public key
openssl rsautl -encrypt -in key.plain -out key.encrypted -pubin -inkey bob.public
# Alice sends Bob:
# - the encrypted message
# - the encrypted key
# - the signed message digest
# Bob decrypts Alice's encrypted key using his private key
openssl rsautl -decrypt -in key.encrypted -out key.decrypted -inkey bob.private
# Bob decrypts the message using the decrypted key
openssl des3 -d -kfile key.decrypted -in message.encrypted -out message.decrypted
# Bob verifies the digest Alice has signed using her public key
openssl rsautl -verify -in digest.signed -out message.digest1 -pubin -inkey alice.public
# Bob calculates again a message digest of the message
openssl dgst -binary message.plain >message.digest2
# Bob compares the two message digests to verify Alice signed the agreement
# he has examined
diff message.digest1 message.digest2
A Simple Public Key System
- Create a graph with a known perfect code
- We draw a set of dominating edges
- Add more edges around each edge
- Add more verices between the non-dominating edges
- The graph is our public key
- The exact dominating set the private key
- Determining whether the graph as a dominating set is NP-complete
- Simple example: fair coin tossing over the phone
- Alice sends map to Bob
- Bob guesses whether number of dominating edges is odd or even
- Alice reveals the solution
- Public key encryption and decryption
- To transmit a secret number
- Randomly distribute the number on all edges
- For each edge send the sum of all its immediate neighbours and itsself
- To decrypt
- Sum the values of the dominating set
Bibliography
- Ross Anderson.
Security Engineering: A Guide to Building Dependable Distributed Systems,
pages 73–113.
John Wiley & Sons, New York, 2001.
- Friedrich L. Bauer.
Decrypted Secrets: Methods and Maxims of Cryptology.
Springer Verlag, 1997.
- Tim Bell, Harold
Thimberly, Mike Fellows, Ian Witten, and Neil Koblitz.
Explaining cryptosystems to the general public.
In Louise Yngström and Simone Fisher-Hübner, editors, WISE 1:
First World Conference on Information Security Education, pages
221–233. IFIP TC11 WG 11.8, June 1999.
- Dorothy Elizabeth Robling
Denning.
Cryptography and Data Security.
Addison-Wesley, 1983.
- Dieter Gollmann.
Computer Security.
John Wiley & Sons, New York, 1999.
- David Kahn.
The
Codebreakers: The Story of Secret Writing.
Scribner, New York, 1996.
- Bruce Schneier.
Applied Cryptography.
Wiley, New York, second edition, 1996.
Access Control, Firewalls and VPNs
Hardware-based Access Control
- Protection problem: prevent processes from interfering
- Confinement problem: prevent prevent non-authorized communication
- Protection rings: levels of protection
- Trusted computing
Operating System Access Control
- Groups and roles
- Access control lists
- Blacklisting and whitelisting
- Capabilities
- Sandboxing
Firewall Purpose
- Restricts people to enter at a carefully controlled point
- Prevents attackers from getting close to other defenses
- Restricts people to leaving at a carefully controlled point
- Firewall can ensure that traffic is acceptable
- Focus of security decisions
- Enforce security policy
- Log network activity
- Limit exposure of one part of the organisation to others
Security Strategies
- Least priviledge: don't allow more than you need
- Defense in depth: have multiple security mechanisms
- Diversity of defence: have different security mechanisms
- Choke point: force attackers to use a narrow channel
- Weakest link: don't divert your attention from them
- Fail safe stance: fail in a way denying access
- Default permit (or deny) stance
- Universal participation: one opt-out can endanger all the rest
- Simplicity
Security by Obscurity
Not effective when it:
- is the only security
- is not real obscurity
- prevents accurate determination of a product's security
- is given irrational confidence
Valid when it:
- helps to avoid vulnerability targetting (hiding equipment and versions)
- complements other measures
- hinders social engineering attacks (e.g. hide hostnames behind firewall)
- is used to protect other measures such as intrusion detection
Firewall Limitations
A firewall can not protect against:
- malicious insiders
- connections that circumvent it
- completely new threats
- some viruses
- the administrator that does not correctly set it up
Firewall Technologies
- Packet filtering
- Proxy services
- Network address translation
- Virtual private network
How Packet Filtering Works
- Determine packet characteristics
- Associate with a network interface (in/outbound)
- Associate with other packets
- reply
- fragmentation
- duplication
- count
- Action:
- Send
- Drop
- Reject (return an error)
- Log
- Raise an alarm
Evaluation of Packet Filtering
- Advantages
- Easy to protect a network through the router
- Efficient
- Widely available
- Disadvantages
- Difficult to setup
- Some prolicies can not be enforced
- Reduces router performance
Basic Packet Filtering
- Naming services--
- DNS (53/udp) to all machines which are not DNS servers, DNS zone transfers (53/tcp) except from external secondaries
- Mail
- SMTP (25/tcp) to all machines, which are not external mail relays
- POP (109/tcp and 110/tcp)
- IMAP (143/tcp)
- Web (except to external Web servers)
- HTTP (80/tcp)
- SSL (443/tcp)
- may also want to block common high-order HTTP port choices (8000/tcp, 8080/tcp, 8888/tcp, etc.)
Other Service Packet Filtering
- Login services:
- telnet (23/tcp)
- SSH (22/tcp)
- FTP (21/tcp)
- NetBIOS (139/tcp)
- rlogin et al (512/tcp through 514/tcp)
- RPC and NFS:
- Portmap/rpcbind (111/tcp and 111/udp)
- NFS (2049/tcp and 2049/udp)
- lockd (4045/tcp and 4045/udp)
- NetBIOS in Windows NT:
135 (tcp and udp), 137 (udp), 138 (udp), 139 (tcp). Windows 2000 - earlier ports plus 445(tcp and udp)
- X Windows:
6000/tcp through 6255/tcp
- Naming services--
- DNS (53/udp) to all machines which are not DNS servers, DNS zone transfers (53/tcp) except from external secondaries
- "Small Services"-- ports below 20/tcp and 20/udp, time (37/tcp and 37/udp)
- Miscellaneous--
- TFTP (69/udp)
- finger (79/tcp)
- NNTP (119/tcp)
- NTP (123/udp)
- LPD (515/tcp)
- syslog (514/udp)
- SNMP (161/tcp and 161/udp, 162/tcp and 162/udp)
- BGP (179/tcp)
- SOCKS (1080/tcp)
- ICMP
- incoming echo request (ping and Windows traceroute)
- outgoing echo replies
- time exceeded
- destination unreachable messages
- Do not block "packet too big" messages (type 3, code 4).
IP Packet Filtering
Block:
- Any packet coming into your network with a source address of your internal network
- Any packet coming into your network not with a destination address of your internal network
- Any packet leaving your network not with a source address of your internal network
- Any packet leaving your network with a destination address of your internal network.
- Any packet coming into your network or leaving your network with a private, loopback, or reserved source or destination address
- 10.x.x.x/8,
- 172.16.x.x/12
- 192.168.x.x/16
- 127.0.0.0/8.
- Source routed packets
- Packets with the IP options field set
- Reserved, DHCP auto-configuration and Multicast addresses
- 0.0.0.0/8
- 169.254.0.0/16
- 192.0.2.0/24
- 224.0.0.0/4
- 240.0.0.0/4
How Proxying Works
- Application level gateway
- Depends on specialised client programs or user procedures
- Can also work transparently with a help of a router
transparent proxy
- Sometimes also associated with caching (e.g. ftp, http)
- Most web clients provide built-in support for proxying
- Some services (SMTP, NNTP) are by default designed to work
with proxy-style gateways
- Proxy technology examples:
- SOCKS
- TIS
- Microsoft Proxy Server
Evaluation of Proxying
- Application level gateway
- Depends on specialised client programs or user procedures
- Can also work transparently with a help of a router
transparent proxy
- Sometimes also associated with caching (e.g. ftp, http)
- Most web clients provide built-in support for proxying
- Some services (SMTP, NNTP) are by default designed to work
with proxy-style gateways
- Proxy technology examples:
- SOCKS
- TIS
- Microsoft Proxy Server
How Network Address Translation Works
- Use reserved IP addresses inside the network
- Map internal addresses to external addresses
- Use different addresses or ports to separate requests
NAT Example
Packets Inside the NAT
14:59:13.710291 eagle.spinellis.gr.1112 > istlab.dmst.aueb.gr.http:
S 3678001010:3678001010(0) win 64240 <mss 1460,nop,nop,sackOK> (DF)
14:59:13.810853 istlab.dmst.aueb.gr.http > eagle.spinellis.gr.1112:
S 881432074:881432074(0) ack 3678001011 win 57344 <mss 1460> (DF)
Packets on the Internet
14:59:13.725267 nat.spinellis.gr.1112 > istlab.dmst.aueb.gr.http:
S 3678001010:3678001010(0) win 64240 <mss 1460,nop,nop,sackOK> (DF)
14:59:13.725285 istlab.dmst.aueb.gr.http > nat.spinellis.gr.1112:
S 881432074:881432074(0) ack 3678001011 win 57344 <mss 1460> (DF)
Evaluation of Network Address Translation
- Advantages
- Enforce control over outbound connections
(internal addresses can not be used)
- Restrict incoming traffic
- Conceal internal network configuration
- Conserve address space
- Disadvantages
- Mapping interferes with stateless IP model
- Confused by embedded IP addresses
- Interferes with authentication and encryption
- Confuses logging
Firewall Architectures
- Screening Router
- Dual-homed Host
- Screened Host
- Screened Subnet
- Internal Firewall
- Personal Firewall
Screening Router
Router configuration set to drop packets.
- Costly if implemented as such
- Cheap if using spare processing capacity of existing router
- Impacts router performance
- May be OK for perimeter, not between administrative boundaries
- Inflexible
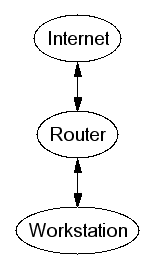
Dual-homed Host
Host with two network adapters, routing often disabled.
- Low cost
- Flexible
- High maintenance
- Not suitable for high bandwidth links
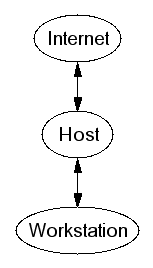
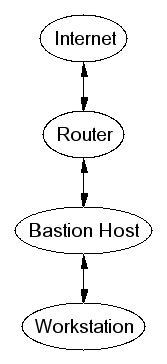
Screened Host
- Router provides packet filters for some basic services
- Bastion host proxies more risky services
- Not suitable for exporting services
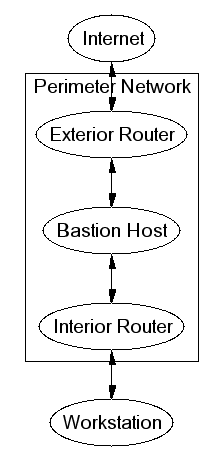
Screened Subnet
- Protects against bastion host gettin cracked
- Suitable for exporting services
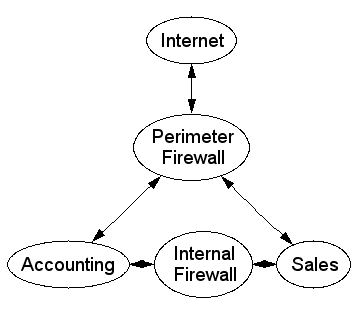
Internal Firewall
- Isolates different administrative domains
- Manages different levels of trust
Personal Firewall
- Software run on workstation
- Handles packets before other services
- Centralized configuration and monitoring point
- Decentralized administration can be a problem
Incident Levels
- Probe: a few tries to break in
- Attack: concerted attempt
- Break-in: host has been compromised
Probe
A few (random) tries to break in.
- Try to access insecure services
- Try common names (anonumous, guest)
- Address probing
- Port scanning
Attack
Concerted break-in attempt.
- Multiple failed attempts to valid accounts
- Attempts over a lengthy period from the same host
- Successful login from unknown site
- Increases in incoming / outgoing traffic
Break-in
Host has been compromised.
- Deleted or modified log files
- Installation of a rootkit
- Programs behave in a strange way
- Unexpected logins to privileged users
- New services running
- Changed login prompt
- New programs running
- Unaxpected changes in disk space usage
- Probes from inside the network
Maintenance: Housekeeping
- Backup
- Manage accounts
- Keep disk clean (so that you can recognise intrusion signs)
- Rotate logs
Maintenance: Monitoring
- Signs for a compromise
- Attacks
- Log
- Dropped and rejected packets
- Denied connections
- Rejected connection attempts
- Username and time of successful connections (bastion hosts)
- Error messages
- Do not log passwords (and failed user names as they might be passwords)
Maintenance: Updating
- Subscribe to mailing lists
- Check vendor patches
- Upgrade when needed (and only then)
VPN Architectures
- Site-to-site: used to connect organisational branches
- Remote access
- Extranet
Tunneling
- Each packet is encapsulated
- Can provide:
- Confidentiality
- Integrity
- Authenticity
Defence in Depth Example
2 Layers
- Firewall
- Host based packet filtering
5 Layers
(Increase security on the Internet side to handle DDOS attacks)
- Border router
- Network management system
- Intrusion detection system
- Firewall
- Host based packet filtering
8 Layers
(Increase security on the workstation side to handle internal attacks)
- Border router
- Network management system
- Intrusion detection system
- Firewall
- Host based packet filtering
- Log analysis and alert
- File integrity validation
- Cryptography
Bibliography
-
Firewalls and Internet Security by Bill Cheswick and Steve Bellovin
- Ross Anderson.
Security Engineering: A Guide to Building Dependable Distributed Systems,
pages 374–378.
John Wiley & Sons, New York, 2001.
- Dieter Gollmann.
Computer Security, pages 224–242.
John Wiley & Sons, New York, 1999.
- Eric Rescorla.
SSL
and TLS.
Addison-Wesley, 2001.
- Elizabeth Zwicky, Simon
Cooper, and D. Brent Chapman.
Building Internet Firewalls.
O'Reilly and Associates, Sebastopol, CA, second edition, 2000.
Web Security and Mobile Code
Web Security Requirements
- Confidentiality (client and server)
- Integrity (client and server)
- Availability (mostly server issue)
User Privacy: What are we Protecting?
- Identity (name, email)
- Location (IP address, domain name, physical location)
- Visited sites
- Search engine input
- Shopping habits
- Form data
Data Traces
Traces are left on:
- Address-bar history
- Local history file
- Local cache
- Cookie file
- Explicitly set proxy log file
- Transparent proxy log file
- Remote log files
- Remote databases
- Packet tracing dumps
Web Server Data
Typical data available to the web server:
GET http://www.google.com/ HTTP/1.1
Host: www.google.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 5.1; en-US; rv:1.6) Gecko/20040113
Accept: application/x-shockwave-flash,text/xml,application/xml,application/xhtml+xml,text/html;q=0.9,text/plain;q=0.8,image/png,image/jpeg,image/gif;q=0.2,*/*;q=0.1
Accept-Language: en-us,en;q=0.8,el;q=0.5,de;q=0.3
Accept-Encoding: gzip,deflate
Accept-Charset: windows-1253,utf-8;q=0.7,*;q=0.7
Keep-Alive: 300
Proxy-Connection: keep-alive
Cookie: PREF=ID=33a5ab74b4a12719:LD=en:CR=2:TM=1070012757:LM=1070012764:S=bEOIfrJZzBGyc5LD
Log File Contents
Normal Users
217.195.129.242 - - [23/Jun/2004:15:38:25 +0300] "GET /pubs/jrnl/2000-IST-Components/html/comp.html HTTP/1.0" 200 49099 "http://find.in.gr/results.page?data=unix+command" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; Q312461)"
217.195.129.242 - - [23/Jun/2004:15:38:25 +0300] "GET /pubs/jrnl/2000-IST-Components/html/process.gif HTTP/1.0" 200 6429 "http://www.spinellis.gr/pubs/jrnl/2000-IST-Components/html/comp.html" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; Q312461)"
backport.reaktor-i.com - - [23/Jun/2004:16:00:05 +0300] "GET /sw/umlgraph/doc/index.html HTTP/1.1" 200 3317 "http://www.spinellis.gr/sw/umlgraph/" "Mozilla/5.0 (X11; U; Linux i686; en-US; rv:1.6) Gecko/20040207 Firefox/0.8"
backport.reaktor-i.com - - [23/Jun/2004:16:00:08 +0300] "GET /sw/umlgraph/doc/cd-intro.html HTTP/1.1" 200 2188 "http://www.spinellis.gr/sw/umlgraph/doc/index.html" "Mozilla/5.0 (X11; U; Linux i686; en-US; rv:1.6) Gecko/20040207 Firefox/0.8"
Crawler
65.197.137.37 - - [22/Jun/2004:13:33:58 +0300] "GET /robots.txt HTTP/1.1" 200 35 "-" "ZipppBot/0.25 (Zippp; http://www.zippp.net; webmaster@zippp.net)"
65.197.137.37 - - [22/Jun/2004:13:33:59 +0300] "GET /pubs/conf/1994-OOPSLA-Multipar/html/mlom.html HTTP/1.1" 200 19166 "-" "ZipppBot/0.25 (Zippp; http://www.zippp.net; webmaster@zippp.net)"
Web Server Exploitation Attempts
[Thu Jun 10 11:36:59 2004] [error] [client 148.244.150.52] script not found or unable to stat: /webdata/istlab-cgi-bin/FormMai
l.pl
[Thu Jun 10 11:37:03 2004] [error] [client 148.244.150.52] script not found or unable to stat: /webdata/istlab-cgi-bin/mail.pl
[Thu Jun 10 11:37:03 2004] [error] [client 148.244.150.52] script not found or unable to stat: /webdata/istlab-cgi-bin/Mail.pl
[Thu Jun 10 11:37:04 2004] [error] [client 148.244.150.52] script not found or unable to stat: /webdata/istlab-cgi-bin/Form.pl
[Thu Jun 10 11:37:04 2004] [error] [client 148.244.150.52] script not found or unable to stat: /webdata/istlab-cgi-bin/form.pl
[Fri Jun 18 23:05:25 2004] [error] [client 216.245.167.136] File does not exist: /webdata/spinellis/_vti_bin/owssvr.dll
[Fri Jun 18 23:05:25 2004] [error] [client 216.245.167.136] File does not exist: /webdata/spinellis/MSOffice/cltreq.asp
[Fri Jun 18 23:06:17 2004] [error] [client 216.245.167.136] File does not exist: /webdata/spinellis/_vti_bin/owssvr.dll
[Fri Jun 18 23:06:18 2004] [error] [client 216.245.167.136] File does not exist: /webdata/spinellis/MSOffice/cltreq.asp
Packet Dump Output
Web Request
02:40:27.881867 192.168.238.1.1540 > 192.168.238.5.www: P 1:485(484) ack 1 win 6
4240 (DF)
0x0000 4500 020c 5af0 4000 8006 40a3 c0a8 ee01 E...Z.@...@.....
0x0010 c0a8 ee05 0604 0050 6a19 984a 87b4 aae9 .......Pj..J....
0x0020 5018 faf0 59b7 0000 4745 5420 2f6f 7267 P...Y...GET./org
0x0030 616e 2d65 6e68 616e 6365 6d65 6e74 2e68 an-enhancement.h
0x0040 746d 6c20 4854 5450 2f31 2e31 0d0a 486f tml.HTTP/1.1..Ho
0x0050 7374 3a20 3139 322e 3136 382e 3233 382e st:.192.168.238.
0x0060 350d 0a55 7365 722d 4167 656e 743a 204d 5..User-Agent:.M
0x0070 6f7a 696c 6c61 2f35 2e30 2028 5769 6e64 ozilla/5.0.(Wind
Password in a Packet Dump
05:50:03.157394 seagull.spinellis.gr.1098 > www.taxisnet.gr.http: P
479:588(109) ack 1 win 16603 (DF)
0x0000 4500 0095 0654 4000 8006 7057 c0a8 880e E....T@...pW....
0x0010 d4cd 6633 044a 0050 fdf4 e5a9 912f e6a5 ..f3.J.P...../..
0x0020 5018 40db 1033 0000 436f 6e74 656e 742d P.@..3..Content-
0x0030 7479 7065 3a20 6170 706c 6963 6174 696f type:.applicatio
0x0040 6e2f 782d 7777 772d 666f 726d 2d75 726c n/x-www-form-url
0x0050 656e 636f 6465 640d 0a43 6f6e 7465 6e74 encoded..Content
0x0060 2d6c 656e 6774 683a 2033 380d 0a0d 0a70 -length:.38....p
0x0070 7764 3d73 6563 7265 7426 7573 6572 6e61 wd=secret&userna <<<
0x0080 6d65 3d74 6573 7475 7365 7226 7061 7373 me=testuser&pass <<<
0x0090 776f 7264 3d word=
Malicious Applets
Once malicious code gets control of the machine it can:
- Compromise the user's privacy
- Actively snoop the user's keystrokes
- Steal resources to:
- Orchestrate a DDoS attack
- Send spam mail
- Spread viruses
- Dial long-distance calls
- Impersonate on behalf of the user (including certificate authentication)
- Distribute sensitive documents
The Java Sandbox Model
- Java code is executed through a virtual machine
- Java applets can contain untrusted code
- Untrusted code is checked for validity
- Untrusted code is executed in a sandbox using an appropriate security policy
Bytecode Verification
Bytecode verification checks that:
- The file is correctly formatted
- The parameter stack will not overflow or underflow
- Bytecode instructions use the correct types
- No invalid type conversions are performed
- No unauthorised member access is performed (through private or protected fields and methods).
- Register accesses follow the legal conventions
Common problems
- Insecure Java implementation (e.g. type checking)
- Inappropriate security policy
Policy Example
As an example the sanbox policy may prohibit:
- Reading local files
- Writing local files
- Deleting local files
- Renaming local files
- Creating directories
- Reading directory contents
- Network connections to machines other than the applet's source
- Waiting for network connections
- Creating new windows
- Changing system settings
- Loading dynamic libraries
- Creating a new clall loader or security manager
- Creating classes that already exist
ActiveX and Code Signing
- ActiveX applets are based on Microsoft's
Component Object Model (COM)
- ActiveX applets can access all the machine's resources
- They are signed with a digital signature to ensure their origin.
- A similar option is also offered for Java code
- Users are supposed to trust signed applets as they trust
retail software
Problems:
- All or nothing proposition
- Who do you trust?
- Programs from trusted sources may contain vulnerabilities
- Programs from trusted sources may unknowingly contain
malicious code (e.g. by linking with a library)
Javascript
- No relation to Java
- Interpreted inside the browser
- Browser and its limited runtime environment act as a sandbox
- Security problems
Exploitation examples:
- Show pop-up windows
- Access the history file
- Read directory contents
- Trick user to send files by email to untrusted sources
- Violate firewall security policies (e.g. by recreating an applet tag)
Cookies
- Needed to maintain state in stateless HTTP
- Useful for e-commerce (e.g. implementing a shopping basket)
- Format:
Name=VALUE; expires=DATE; domain=DOMAIN; path=PATH; secure
- Example:
www.in.gr FALSE / FALSE 2051222309 SITESERVER ID=8b048791364ee52dfc1d627045d5c58c
.google.com TRUE / FALSE 2147361448 PREF ID=33a5ab94b4a12719:LD=en:CR=2:TM=1070212757:LM=1074012764:S=bEbIgrJZzBGyc5LD
.yahoo.com TRUE / FALSE 1271361609 U mt=Kl4g_p8MhYuN9bHjdexUb81uQuDrHYcx_oFi1Q--&ux=Sqf7/A&un=febgmfte1juft
- Only the same host can access a cookie
Security problems
- The cookie file stores unencrypted personal data over an extended period
- Can be subverted by DNS spoofing
- Therefore an attacker can access personal data (e.g. shopping habits)
- Other users of a machine can access the cookie file
- Problems when cookies are used to make authorisation easier
User Authentication
- The basic authentication method transmits the password unencrypted
Example
POST /cgi-bin/smswww HTTP/1.0
Referer: http://www.netcs.com/pages/foo/send.html
Proxy-Connection: Keep-Alive
User-Agent: Mozilla/3.01 (Win95; I)
Host: www.netcs.com
Accept: image/gif, image/x-xbitmap, image/jpeg, image/pjpeg, */*
Content-type: application/x-www-form-urlencoded
Content-length: 143
Authorization: Basic aWV0ZopqZXRm
- Only useful for "advisory locks"
- Better authentication should be implemented through an SSL link and
custom application code
- Cookies should not be used for authentication
Application-layer Attacks
- Scripting vulnerabilities
- Buffer overflows
- Cookie poisoning
- Hidden field manipulation
- Parameter tampering
- Cross-site scripting
- SQL injection
Server Security and Scripting
- Server-side scripting (ASP, PHP, mod_perl, CGI) uses interpreted languages
(Visual Basic, PHP, sh, Perl, Tcl, Java, Python)
- Can be used by attackers to execute code on the server
- Compromise the web server (e.g. change security model)
- Compromise the database
- Compromise the host
Scripting Exploitation Example
The following flawed and insecure Perl program is
supposed to run the Unix "finger" command for the user
given on a form's USER field:
#!/usr/bin/perl
$query = $ENV{'QUERY_STRING'};
@pairs = split(/\&/, $query);
for (@pairs) {
($field, $val) = split(/=/);
$field =~ s/\+/ /g;
$field =~ s/\%(\w\w)/sprintf("%c", hex($1))/eg;
$val =~ s/\+/ /g;
$val =~ s/\%(\w\w)/sprintf("%c", hex($1))/eg;
$field{$field} = $val;
}
$|=1;
print "Content-Type: text/plain\n\n";
system "finger $field{USER}\n";
Running the program with USER having the value "dds"
http://www.host.gr/cgi-bin/pe?USER=dds
will give the following result:
Login: dds Name: Diomidis Spinellis
Directory: /home/dds Shell: /bin/bash
On since Wed Jun 30 12:18 (EET) on ttyp0
5 minutes 49 seconds idle
Adding to the URI a semicolon (the Unix shell command separator)
and the command cat /etc/shadow
http://www.host.gr/cgi-bin/pe?USER=dds;cat%20/etc/shadow
may send us the encoded contents of the system's password
file after the results of the finger command.
Login: dds Name: Diomidis Spinellis
Directory: /home/dds Shell: /bin/bash
On since Wed Jun 30 12:18 (EET) on ttyp0
5 minutes 49 seconds idle
root:XXXXXXXXXXXXX:0:0:Charlie Root:/root:/bin/bash
bin:*:1:1:bin:/bin:
daemon:*:2:2:The Devil Himself:/sbin:
adm:*:3:4:adm:/var/adm:
lp:*:4:7:lp:/var/spool/lpd:
...
Scripting Guidelines
To avoid exploitation problems:
- Run the server as a non-priviledged user
- Maintain the server's host security
- Avoid scripting languages on web servers
- Do not trust form data
- Check all user data and remove all metacharacters
State Variable Manipulation
- The HTTP protocol is stateless
- A number of different mechanisms are used to store state:
- Cookies
- Hidden fields
- Parameters
- These entities are typically not protected
- Attackers can manipulate these entities to alter their identity or authorization
Cross-site Scripting
- Attacker stores script on victim site
- Attacker tricks user into executing script
- Victim user enters confidential data
- Attacker uses confidential data against victim user
Bibliography
-
Practical UNIX and Internet Security, 2nd Edition by Simson Garfinkel and Gene Spafford
- Ross Anderson.
Security Engineering: A Guide to Building Dependable Distributed Systems,
pages 367–371, 379–388.
John Wiley & Sons, New York, 2001.
- David Geer.
E-micropayements sweat the small stuff.
Computer, 37(8):19–22, August 2004.
- Dieter Gollmann.
Computer Security, pages 186–199.
John Wiley & Sons, New York, 1999.
- U. Homann, M. Rill, and
A. Wimmer.
Flexible value structures in banking.
Communications of the ACM, 47(5):34–36, May 2004.
- Michael Howard and
David LeBlanc.
Writing Secure Code, pages 413–438, 477–516.
Microsoft Press, Redmond, WA, second edition, 2003.
- Gary McGraw and
Edward W. Felten.
Securing Java: Getting Down to Business with Mobile Code.
Wiley, New York, 1999.
- Aviel D. Rubin, Daniel
Geer, and Marcus J. Ranum.
Web
Security Sourcebook.
John Wiley & Sons, New York, 1997.
- Victoria
Skoularidou and Diomidis Spinellis.
Security architectures for network clients ( http://www.spinellis.gr/pubs/jrnl/2003-IMCS-clisec/html/cli-sec.html).
Information Management and Computer Security, 11(2):84–91,
2003.
Appendix A: Protecting the Internet Explorer
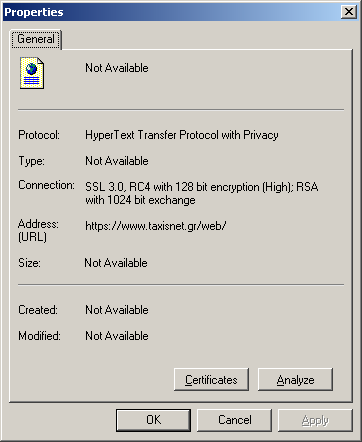
Information of a secure page
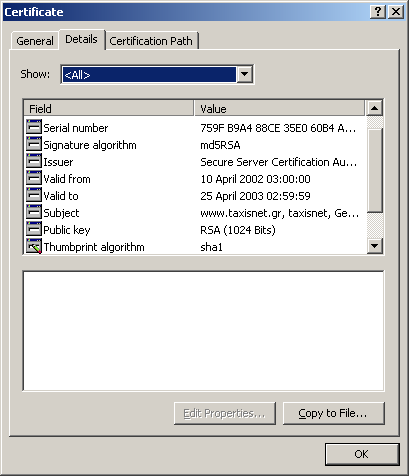
Page certificate information
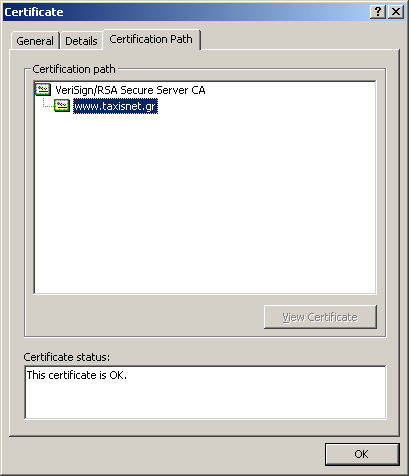
Certification path
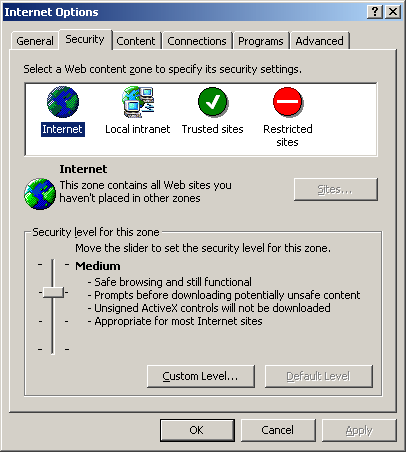
Basic security settings
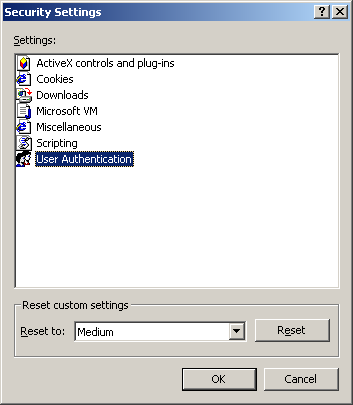
Tailored security settings
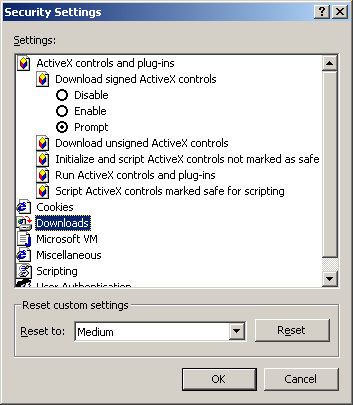
ActiveX controls
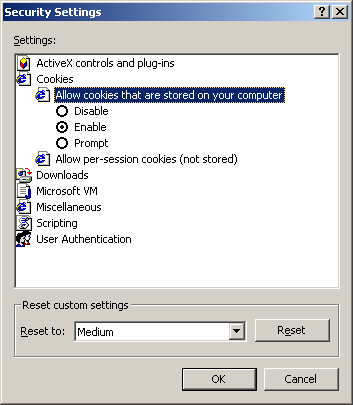
Cookies
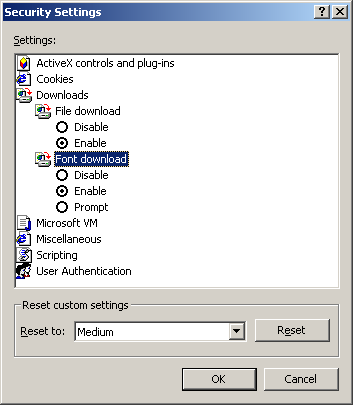
Downloads
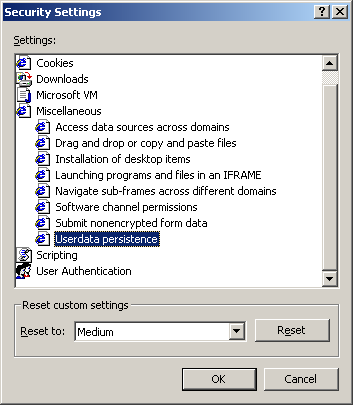
Microsoft extensions
Scripting
Authentication
Security implementation
Appendix B: Protecting Mozilla
Mozilla places privacy and security and devotes a number of configuration
options for this task.
Privacy categories
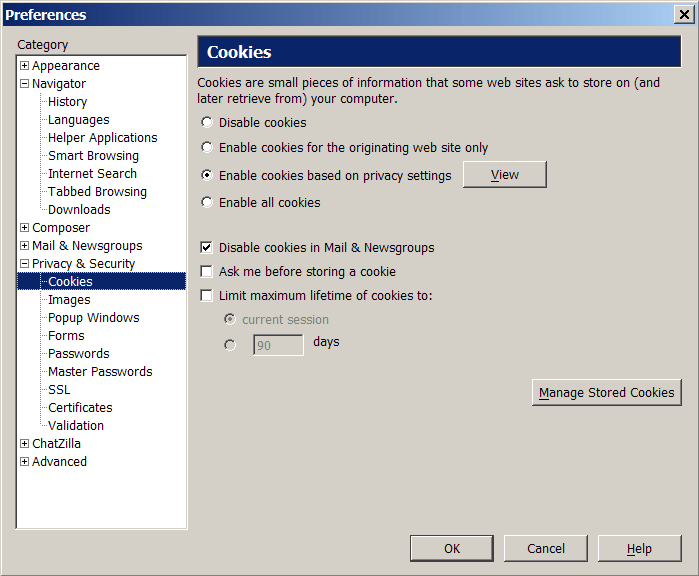
Cookie management
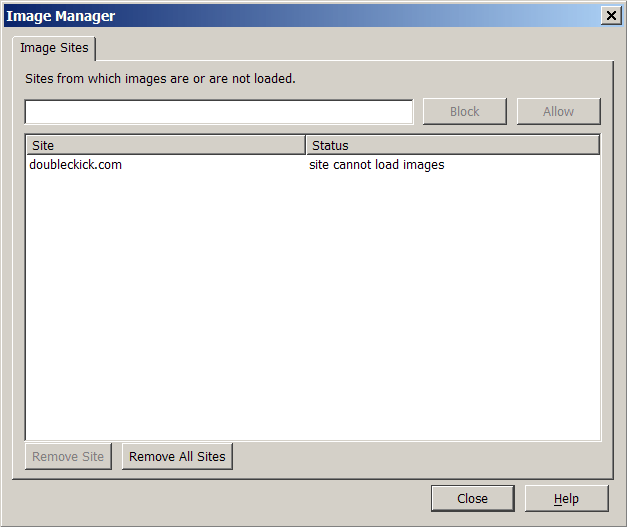
Image management
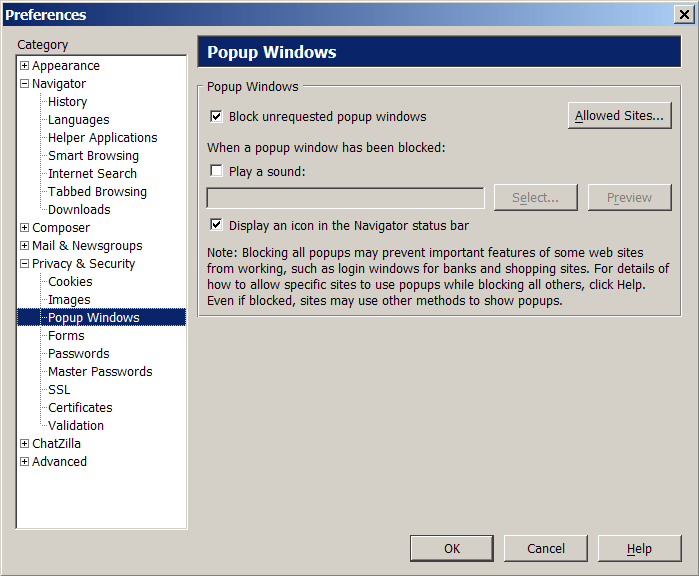
Popup window management
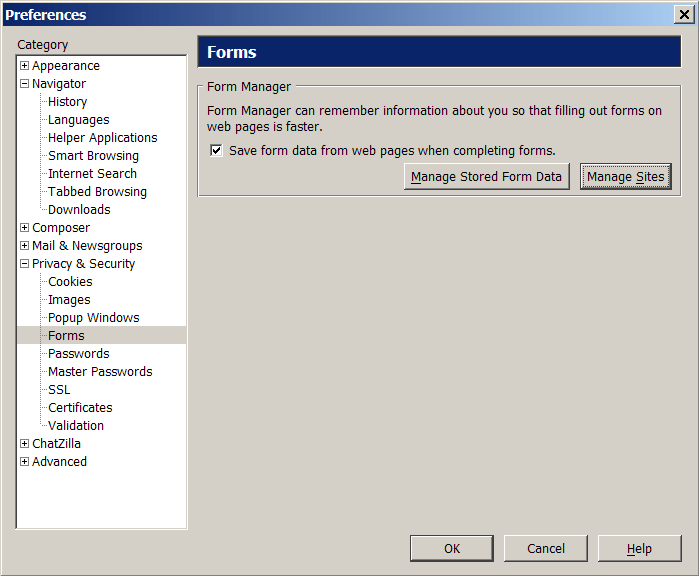
Form management
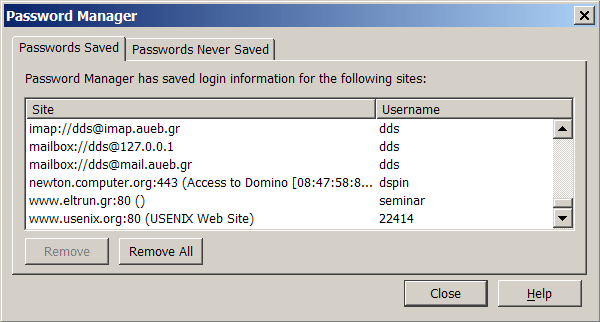
Password management
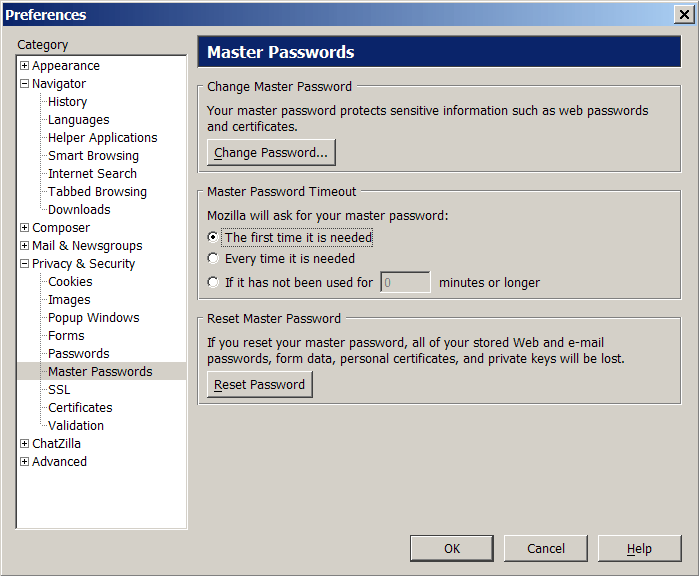
Master password
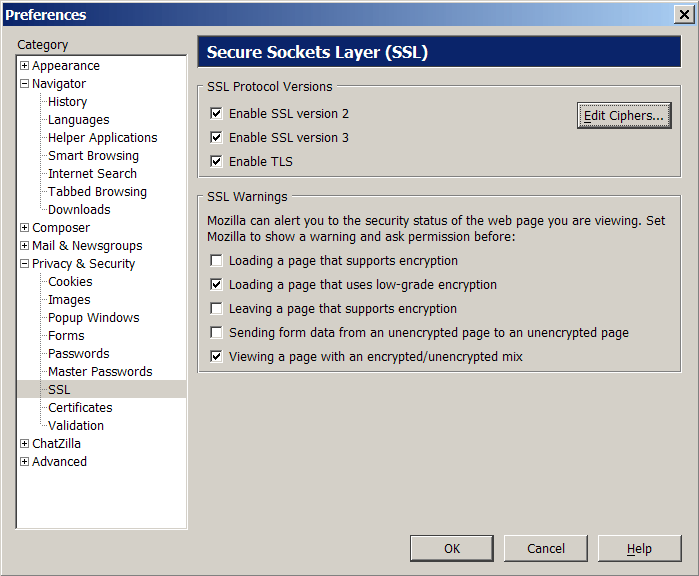
SSL details
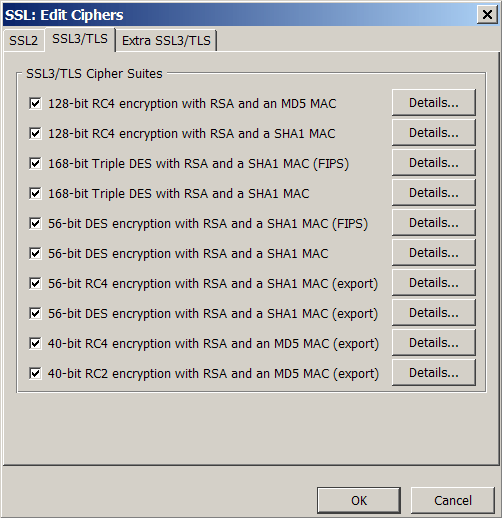
Cipher options
Certificate options
Certificate authorities
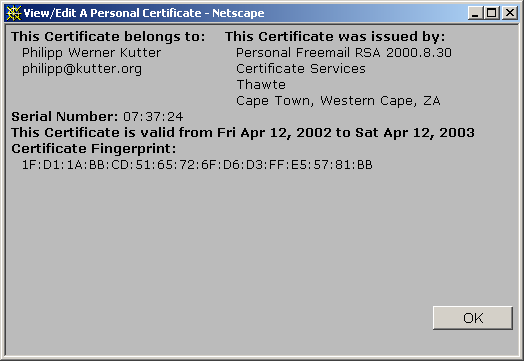
Personal certificate details
Certificate validation
Appendix C: Protecting the Netscape Navigator
Executable content
Content security information
Certificate information
Secure page view
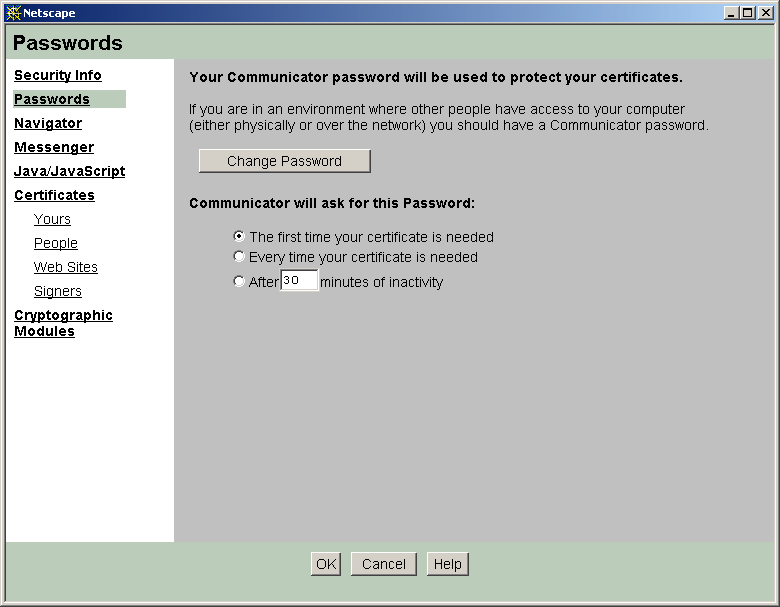
Password security
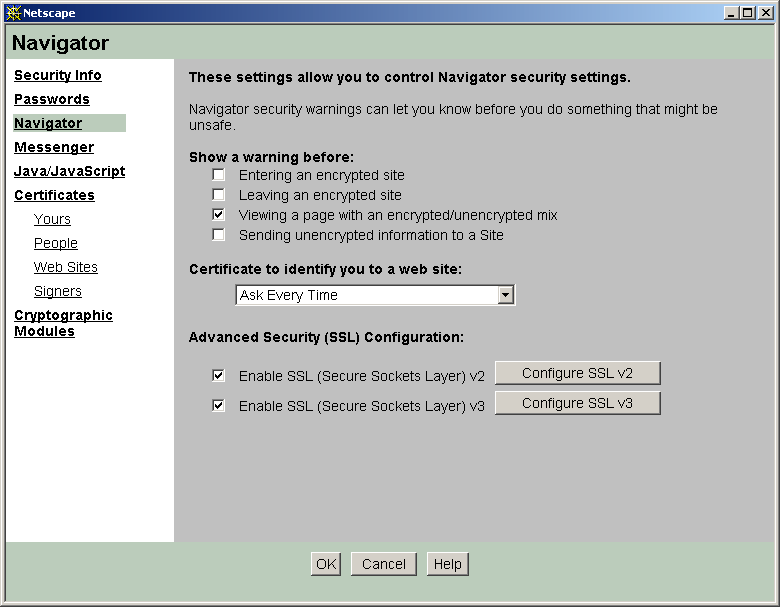
Browser settings
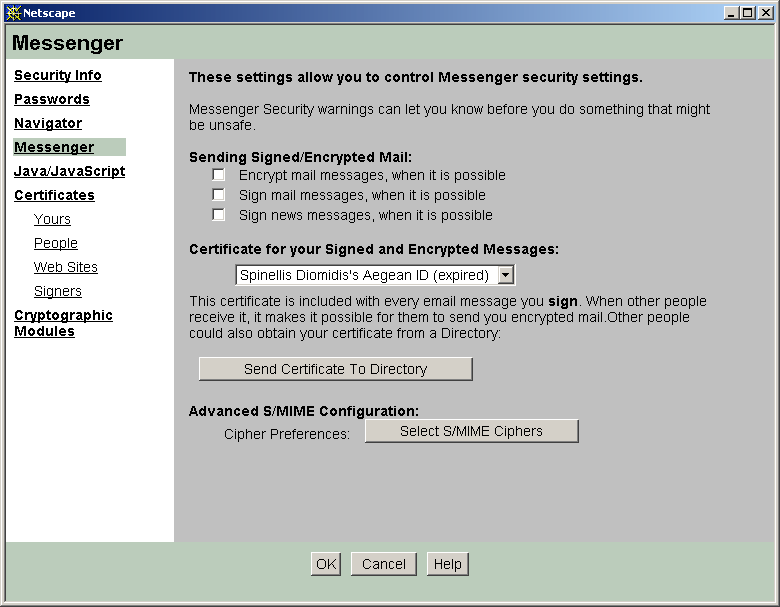
Mail settings
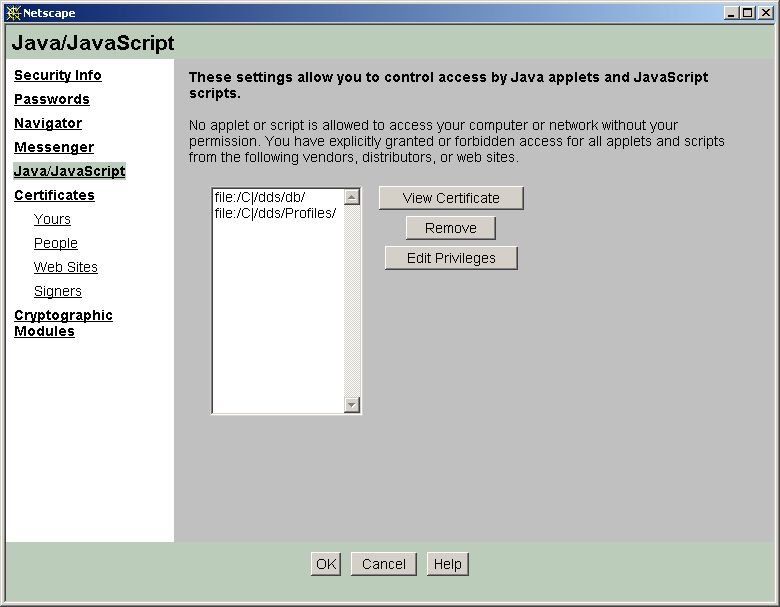
Signed executable content
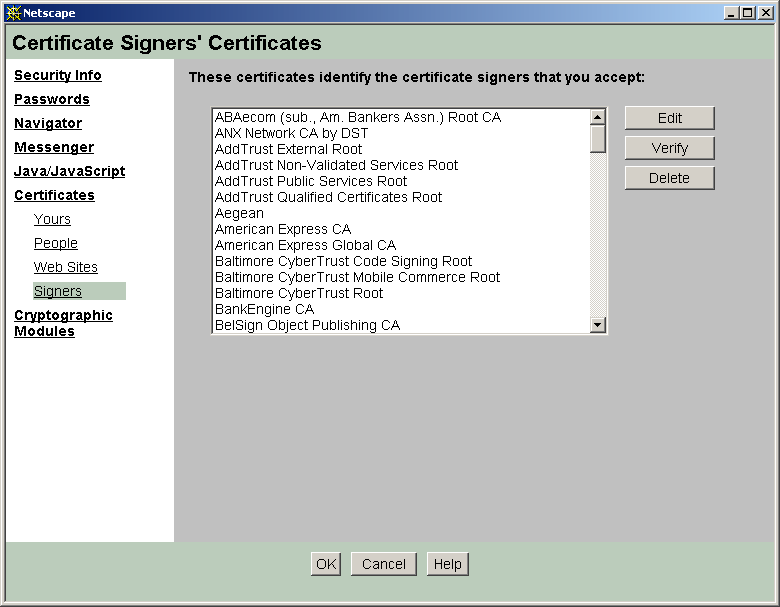
Certificates and CAs
Personal Certificate
Cryptography
Cryptographic module access
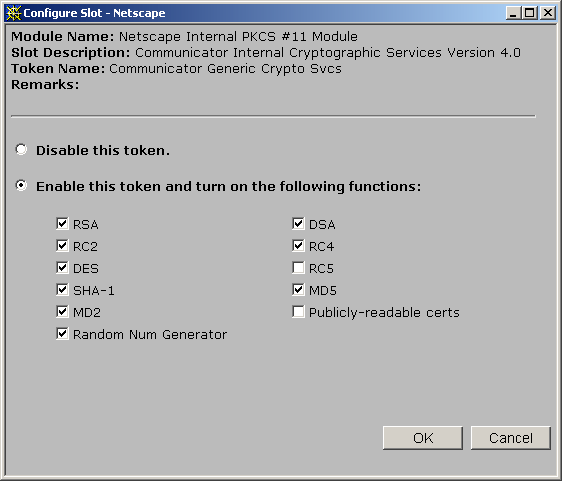
Cryptographic algorithms
Software Security
Principles for Software Security
- Secure the weakest link
Example:
social engineering attacks; attacks agains applications vs firewalls
- Defense in depth
Example:
use a VPN and encrypt your data
- Fail securely
Counterexample:
Pressing Esc on the Windows 95/98/Me login screen
(with domain login dissabled)
- Principle of least Privilege
Counterexample:
Unix programs running with superooser privileges.
Example: sendmail submission user.
- Compartmentalize
Counterexample:
Outlook HTML rendering engine.
- Keep it simple
Example:
choke point e.g. firewall.
Counterexample: security protocols, they are complex by neccessity, but
flaws are often found years after their introduction.
- Do not volunteer information
Example:
$ telnet relay2.ucia.gov smtp
Trying 198.81.129.194...
Connected to relay2.ucia.gov.
Escape character is '^]'.
220 ain-relay2.net.cia.gov SMTP Ready.
HELO aueb.gr
250 (aueb.gr) pleased to meet you.
Counterexample:
$ telnet mail.aueb.gr smtp
Trying 195.251.255.142...
Connected to hermes.aueb.gr.
Escape character is '^]'.
220 hermes.aueb.gr ESMTP Sendmail 8.12.9/8.12.9; Fri, 4 Jul 2003 12:53:14 +0300
HELO aueb.gr
250 hermes.aueb.gr Hello istlab.dmst.aueb.gr [195.251.253.207], pleased to meet you
- Hiding secrets is close to impossible
Example:
DVD DeCSS
- Be reluctant to trust
Counterexample:
downloading software
- Use community resources
Example:
public cryptographic algorithms and their implementations.
Buffer Overflows
- Cause of around 20-50% of all CERT security alerts
- Simple example (DOS attack)
$ cat bufftest.c
main()
{
char buff[20];
gets(buff);
puts(buff);
}
$ cc -o bufftest bufftest.c
/tmp/ccjCiHlw.o: In function `main':
/tmp/ccjCiHlw.o(.text+0xe): warning: this program uses gets(), which is unsafe.
$ ./bufftest
warning: this program uses gets(), which is unsafe.
normal text
normal text
$ ./bufftest
warning: this program uses gets(), which is unsafe.
text longer than the buffer size
text longer than the buffer size
Segmentation fault (core dumped)
How does a Buffer Overflow Work?
The attacker can execute code by corrupting the stack
This is the stack when gets is called:
+---------------+
| envp | Program's environment
+---------------+
| argv | Argument vector
+---------------+
| argc | Argument count
+---------------+
| _start | Return address of main
+---------------+
| buff[0] | First byte of buffer (e.g. 'n')
+---------------+
| buff[1] | Second byte of buffer (e.g. 'o')
+---------------+
| buff[...] | More buffer bytes
+---------------+
| buff[19] | Last byte of buffer
+---------------+
| main+12 | Return address of gets
+---------------+
This is the corrupted stack after an attack:
+---------------+
| envp | Program's environment
+---------------+
| argv | Argument vector
+---------------+
| argc | Argument count
+---------------+
| _start | Return address of main
+---------------+
| buff[0] |<-+ First byte of buffer (EVIL CODE)
+---------------+ |
| buff[1] | | Second byte of buffer (EVIL CODE)
+---------------+ |
| buff[...] | | More buffer bytes (more EVIL CODE)
+---------------+ |
| buff[19] | | Last byte of buffer
+---------------+ |
| &buff[0] |--^ Overwritten return address
+---------------+
Buffer Overflow Defences
- Use a language with strong typing and array checking
- Avoid fixed buffers
- Avoid unchecked routines using fixed buffers (e.g. gets, strcpy)
- Use routines that have buffer length as an argument (e.g. fgets, strncpy)
- Use libraries and execution environments that protect against stack
smashing attacks
- When writing to a fixed buffer, check index against the buffer's size
Unix Access Control
- Every user has a (typically unique) identifier
- Each user belongs to one or more groups
Example:
$ id
uid=1000(dds) gid=1000(dds) groups=1000(dds), 0(wheel), 10000(cvs), 20000(lh), 20001(dynweb), 20002(rpipe), 20003(postg), 20004(issues), 20005(dewdrop), 20006(eaware), 20007(mexpress), 20008(ivm), 20009(weblog), 20010(rng), 20011(uca)
- Each file belongs to a user and a group
- Each file or directory has a set of permissions associated with it
- Permissions are: write access, read access, execute permission
- A different permission set is specified for the file's user, group,
and all other users.
- On directories execute permission implies ability to traverse
- Executable files can be specified to run under the permission of their
owner or group (rather than the user executing them).
- A sepcial user, the super user (named root overrides all
access permissions
Example:
-r-xr-xr-x 1 root wheel 206740 Mar 27 15:42 /usr/bin/make
-r-sr-xr-x 1 man wheel 29752 Mar 27 15:39 /usr/bin/man
-r-sr-xr-x 2 root wheel 28828 Mar 27 15:42 /usr/bin/passwd
drwxr-xr-x 23 root wheel 1024 Jun 15 16:38 /usr/src
drwxrwxrwt 3 root wheel 512 Jul 4 13:24 /usr/tmp
drwxr-xr-x 2 root wheel 512 Dec 2 2002 /usr/var
drwxr-xr-x 13 root wheel 512 Jun 15 17:01 /usr/www
-rw------- 1 root wheel 5291 Jul 2 12:47 /etc/master.passwd
Windows Access Control
- Users belong to groups
- Preconfigured groups with useful default permissions
- Permissions to files are fine grained:
- File permissions can be specified for users, groups, or abstract entities
- Can also specify auditing on an element basis
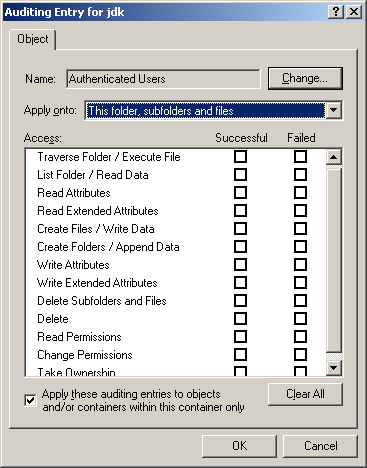
- Audit can generate log entries for success or failure
- A policy editor allows the centralized specification of the security policy
- Comprehensive, but complex system.
Few users and administrators understand it and use it correctly.
Race Conditions
- Expose a window of vulnerability
- Time of check different from time of use (TOCTOU)
and not an atomic operation
- Vulnerable:
- System objects (e.g. files) accessed across system calls (not atomic operations)
- Program objects (e.g. variables) in multithreaded programs
- Example:
if (can_access(file))
/* Window of vulnerability */
write_new_conents(file)
The attacker can:
$ touch my_file
$ privileged_program my_file &
$ rm my_file # Must be executed within the window
$ ln -s /etc/passwd my_file # Must be executed within the window
- Countermeasures:
- Use atomic operations (e.g. open/rename can create/rename a file or fail if the target file exists)
- Use locking in multithreaded programs (e.g. synchronized in Java code)
Problematic APIs
- Functions Susceptible to Buffer Overflows
- Format String Vulnerabilities
- Path and Shell Metacharacter Vulnerabilities
- Temporary Files
- Functions Unsuitable for Cryptographic Use
- Forgeable Data
Randomness and Determinism
Applying Cryptography
- Do not implement functions from scratch
- Use a crypto API (e.g. OpenSSL, Microsoft CryptoAPI)
- Careful on how you apply the primitives (e.g. avoid DES ECB mode)
- Careful on how you manage your keys
- Destroy data and keys when no more needed
Trust Management
- Trust is transitive
- Do not trust other programs you invoke (e.g. editor from a restricted shell)
- Do not trust input you do not control (e.g. hidden web fields)
- Do not trust code you do not control (e.g. Javascript validation)
- Be careful with metacharacters and interpreted languages
(Perl, SQL, sh, PHP, ASP)
Untrusted Input
- Environment variables
- Network data (e.g. DNS)
Result Verification
Failing to check the success of the Unix system calls
setuidsetegidsetgroups
or the Windows API calls
RpcImpersonateClientImpersonateLoggedOnUserCoImpersonateClientImpersonateNamedPipeClientImpersonateDdeClientWindowImpersonateSecurityContextImpersonateAnonymousTokenImpersonateSelfSetThreadToken
can result in a process running with elevated privileges.
Data and Privilege Leakage
Often consequence of discretionary access control.
- Data leakage
- Privilege leakage
- The Java approach
- Isolating privileged code
Password Authentication
- Check for good passwords when they are selected.
Dissallow:
- Short passwords
- Username appearing in password
- Only digits
- Only numbers
- Words in the dictionary (uppercase, lowercase, mixed)
- Do not store the encrypted password;
use the password to encrypt a known key.
- Protected the password databse to prevent dictionary attacks.
- Keep track of failed login attempts
- Even better, use variable passwords like SecureID

Database Security
- Communication is typically unencrypted, therefore restrict it
beyond the firewall.
- Enforce database level security
- Create database users
- Grant access for specific objects and actions (SELECT, INSERT, DELETE, UPDATE)
- Use separate users and permissions for web and maintenance access.
- Careful where you store the database access passwords (client applications)
- Keep in mind statistical attacks
Application Security
Copy protection measures:
- Floating network licenses
- Hardware dongles
- Node locking
Tamperproofing:
- Add antidebugging measures
- Checksum the code
- Plant decoys
- Avoid direct responses
- Code obfuscation
- Code and data encryption
Keep in mind that the attacker has complete control of your application.
Bibliography
- Matt Bishop and
Michael Dilger.
Checking for race conditions in file accesses.
Computing Systems, 9(2):131–152, Spring 1996.
- Michael Howard and
David LeBlanc.
Writing Secure Code.
Microsoft Press, Redmond, WA, second edition, 2003.
- Gary McGraw and
Edward W. Felten.
Securing Java: Getting Down to Business with Mobile Code.
Wiley, New York, 1999.
- Diomidis Spinellis.
Reflection as a mechanism for software integrity verification ( http://www.spinellis.gr/pubs/jrnl/1999-TISS-Reflect/html/reflect.html).
ACM Transactions on Information and System Security, 3(1):51–62,
February 2000.
- John Viega and Gary
McGraw.
Building Secure Software: How to Avoid Security Problems the Right Way.
Addison-Wesley, 2001.
- J. Viega, J. T. Bloch,
Y. Kohno, and G. McGraw.
Its4: A static vulnerability scanner for c and c++ code.
In Proceedings of the 16th Annual Computer Security Applications
Conference (ACSAC'00), page 257. IEEE Computer Society, 2000.




















































