Access Control, Firewalls and VPNs
Diomidis Spinellis
Department of Management Science and Technology
Athens University of Economics and Business
Athens, Greece
dds@aueb.gr
Hardware-based Access Control
- Protection problem: prevent processes from interfering
- Confinement problem: prevent prevent non-authorized communication
- Protection rings: levels of protection
- Trusted computing
Operating System Access Control
- Groups and roles
- Access control lists
- Blacklisting and whitelisting
- Capabilities
- Sandboxing
Firewall Purpose
- Restricts people to enter at a carefully controlled point
- Prevents attackers from getting close to other defenses
- Restricts people to leaving at a carefully controlled point
- Firewall can ensure that traffic is acceptable
- Focus of security decisions
- Enforce security policy
- Log network activity
- Limit exposure of one part of the organisation to others
Security Strategies
- Least priviledge: don't allow more than you need
- Defense in depth: have multiple security mechanisms
- Diversity of defence: have different security mechanisms
- Choke point: force attackers to use a narrow channel
- Weakest link: don't divert your attention from them
- Fail safe stance: fail in a way denying access
- Default permit (or deny) stance
- Universal participation: one opt-out can endanger all the rest
- Simplicity
Security by Obscurity
Not effective when it:
- is the only security
- is not real obscurity
- prevents accurate determination of a product's security
- is given irrational confidence
Valid when it:
- helps to avoid vulnerability targetting (hiding equipment and versions)
- complements other measures
- hinders social engineering attacks (e.g. hide hostnames behind firewall)
- is used to protect other measures such as intrusion detection
Firewall Limitations
A firewall can not protect against:
- malicious insiders
- connections that circumvent it
- completely new threats
- some viruses
- the administrator that does not correctly set it up
Firewall Technologies
- Packet filtering
- Proxy services
- Network address translation
- Virtual private network
How Packet Filtering Works
- Determine packet characteristics
- Associate with a network interface (in/outbound)
- Associate with other packets
- reply
- fragmentation
- duplication
- count
- Action:
- Send
- Drop
- Reject (return an error)
- Log
- Raise an alarm
Evaluation of Packet Filtering
- Advantages
- Easy to protect a network through the router
- Efficient
- Widely available
- Disadvantages
- Difficult to setup
- Some prolicies can not be enforced
- Reduces router performance
Basic Packet Filtering
- Naming services--
- DNS (53/udp) to all machines which are not DNS servers, DNS zone transfers (53/tcp) except from external secondaries
- Mail
- SMTP (25/tcp) to all machines, which are not external mail relays
- POP (109/tcp and 110/tcp)
- IMAP (143/tcp)
- Web (except to external Web servers)
- HTTP (80/tcp)
- SSL (443/tcp)
- may also want to block common high-order HTTP port choices (8000/tcp, 8080/tcp, 8888/tcp, etc.)
Other Service Packet Filtering
- Login services:
- telnet (23/tcp)
- SSH (22/tcp)
- FTP (21/tcp)
- NetBIOS (139/tcp)
- rlogin et al (512/tcp through 514/tcp)
- RPC and NFS:
- Portmap/rpcbind (111/tcp and 111/udp)
- NFS (2049/tcp and 2049/udp)
- lockd (4045/tcp and 4045/udp)
- NetBIOS in Windows NT:
135 (tcp and udp), 137 (udp), 138 (udp), 139 (tcp). Windows 2000 - earlier ports plus 445(tcp and udp)
- X Windows:
6000/tcp through 6255/tcp
- Naming services--
- DNS (53/udp) to all machines which are not DNS servers, DNS zone transfers (53/tcp) except from external secondaries
- "Small Services"-- ports below 20/tcp and 20/udp, time (37/tcp and 37/udp)
- Miscellaneous--
- TFTP (69/udp)
- finger (79/tcp)
- NNTP (119/tcp)
- NTP (123/udp)
- LPD (515/tcp)
- syslog (514/udp)
- SNMP (161/tcp and 161/udp, 162/tcp and 162/udp)
- BGP (179/tcp)
- SOCKS (1080/tcp)
- ICMP
- incoming echo request (ping and Windows traceroute)
- outgoing echo replies
- time exceeded
- destination unreachable messages
- Do not block "packet too big" messages (type 3, code 4).
IP Packet Filtering
Block:
- Any packet coming into your network with a source address of your internal network
- Any packet coming into your network not with a destination address of your internal network
- Any packet leaving your network not with a source address of your internal network
- Any packet leaving your network with a destination address of your internal network.
- Any packet coming into your network or leaving your network with a private, loopback, or reserved source or destination address
- 10.x.x.x/8,
- 172.16.x.x/12
- 192.168.x.x/16
- 127.0.0.0/8.
- Source routed packets
- Packets with the IP options field set
- Reserved, DHCP auto-configuration and Multicast addresses
- 0.0.0.0/8
- 169.254.0.0/16
- 192.0.2.0/24
- 224.0.0.0/4
- 240.0.0.0/4
How Proxying Works
- Application level gateway
- Depends on specialised client programs or user procedures
- Can also work transparently with a help of a router
transparent proxy
- Sometimes also associated with caching (e.g. ftp, http)
- Most web clients provide built-in support for proxying
- Some services (SMTP, NNTP) are by default designed to work
with proxy-style gateways
- Proxy technology examples:
- SOCKS
- TIS
- Microsoft Proxy Server
Evaluation of Proxying
- Application level gateway
- Depends on specialised client programs or user procedures
- Can also work transparently with a help of a router
transparent proxy
- Sometimes also associated with caching (e.g. ftp, http)
- Most web clients provide built-in support for proxying
- Some services (SMTP, NNTP) are by default designed to work
with proxy-style gateways
- Proxy technology examples:
- SOCKS
- TIS
- Microsoft Proxy Server
How Network Address Translation Works
- Use reserved IP addresses inside the network
- Map internal addresses to external addresses
- Use different addresses or ports to separate requests
NAT Example
Packets Inside the NAT
14:59:13.710291 eagle.spinellis.gr.1112 > istlab.dmst.aueb.gr.http:
S 3678001010:3678001010(0) win 64240 <mss 1460,nop,nop,sackOK> (DF)
14:59:13.810853 istlab.dmst.aueb.gr.http > eagle.spinellis.gr.1112:
S 881432074:881432074(0) ack 3678001011 win 57344 <mss 1460> (DF)
Packets on the Internet
14:59:13.725267 nat.spinellis.gr.1112 > istlab.dmst.aueb.gr.http:
S 3678001010:3678001010(0) win 64240 <mss 1460,nop,nop,sackOK> (DF)
14:59:13.725285 istlab.dmst.aueb.gr.http > nat.spinellis.gr.1112:
S 881432074:881432074(0) ack 3678001011 win 57344 <mss 1460> (DF)
Evaluation of Network Address Translation
- Advantages
- Enforce control over outbound connections
(internal addresses can not be used)
- Restrict incoming traffic
- Conceal internal network configuration
- Conserve address space
- Disadvantages
- Mapping interferes with stateless IP model
- Confused by embedded IP addresses
- Interferes with authentication and encryption
- Confuses logging
Firewall Architectures
- Screening Router
- Dual-homed Host
- Screened Host
- Screened Subnet
- Internal Firewall
- Personal Firewall
Screening Router
Router configuration set to drop packets.
- Costly if implemented as such
- Cheap if using spare processing capacity of existing router
- Impacts router performance
- May be OK for perimeter, not between administrative boundaries
- Inflexible
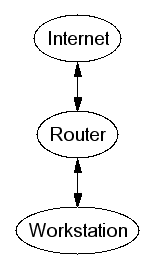
Dual-homed Host
Host with two network adapters, routing often disabled.
- Low cost
- Flexible
- High maintenance
- Not suitable for high bandwidth links
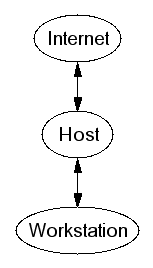
Screened Host
- Router provides packet filters for some basic services
- Bastion host proxies more risky services
- Not suitable for exporting services
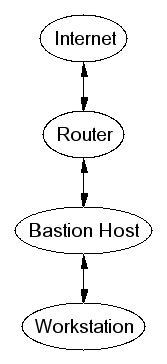
Screened Subnet
- Protects against bastion host gettin cracked
- Suitable for exporting services
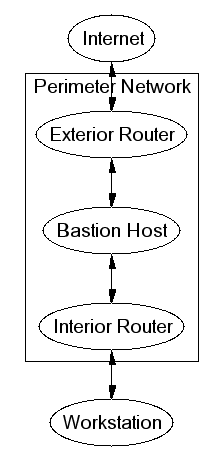
Internal Firewall
- Isolates different administrative domains
- Manages different levels of trust
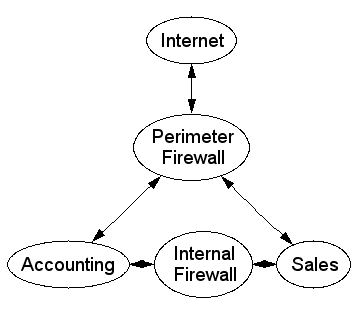
Personal Firewall
- Software run on workstation
- Handles packets before other services
- Centralized configuration and monitoring point
- Decentralized administration can be a problem
Incident Levels
- Probe: a few tries to break in
- Attack: concerted attempt
- Break-in: host has been compromised
Probe
A few (random) tries to break in.
- Try to access insecure services
- Try common names (anonumous, guest)
- Address probing
- Port scanning
Attack
Concerted break-in attempt.
- Multiple failed attempts to valid accounts
- Attempts over a lengthy period from the same host
- Successful login from unknown site
- Increases in incoming / outgoing traffic
Break-in
Host has been compromised.
- Deleted or modified log files
- Installation of a rootkit
- Programs behave in a strange way
- Unexpected logins to privileged users
- New services running
- Changed login prompt
- New programs running
- Unaxpected changes in disk space usage
- Probes from inside the network
Maintenance: Housekeeping
- Backup
- Manage accounts
- Keep disk clean (so that you can recognise intrusion signs)
- Rotate logs
Maintenance: Monitoring
- Signs for a compromise
- Attacks
- Log
- Dropped and rejected packets
- Denied connections
- Rejected connection attempts
- Username and time of successful connections (bastion hosts)
- Error messages
- Do not log passwords (and failed user names as they might be passwords)
Maintenance: Updating
- Subscribe to mailing lists
- Check vendor patches
- Upgrade when needed (and only then)
VPN Architectures
- Site-to-site: used to connect organisational branches
- Remote access
- Extranet
Tunneling
- Each packet is encapsulated
- Can provide:
- Confidentiality
- Integrity
- Authenticity
Defence in Depth Example
2 Layers
- Firewall
- Host based packet filtering
5 Layers
(Increase security on the Internet side to handle DDOS attacks)
- Border router
- Network management system
- Intrusion detection system
- Firewall
- Host based packet filtering
8 Layers
(Increase security on the workstation side to handle internal attacks)
- Border router
- Network management system
- Intrusion detection system
- Firewall
- Host based packet filtering
- Log analysis and alert
- File integrity validation
- Cryptography
Bibliography
-
Firewalls and Internet Security by Bill Cheswick and Steve Bellovin
- Ross Anderson.
Security Engineering: A Guide to Building Dependable Distributed Systems,
pages 374–378.
John Wiley & Sons, New York, 2001.
- Dieter Gollmann.
Computer Security, pages 224–242.
John Wiley & Sons, New York, 1999.
- Eric Rescorla.
SSL
and TLS.
Addison-Wesley, 2001.
- Elizabeth Zwicky, Simon
Cooper, and D. Brent Chapman.
Building Internet Firewalls.
O'Reilly and Associates, Sebastopol, CA, second edition, 2000.
 Last change: Monday, August 2, 2004 12:27 am
Last change: Monday, August 2, 2004 12:27 am




